Malware analysis Malicious activity
Por um escritor misterioso
Last updated 01 junho 2024
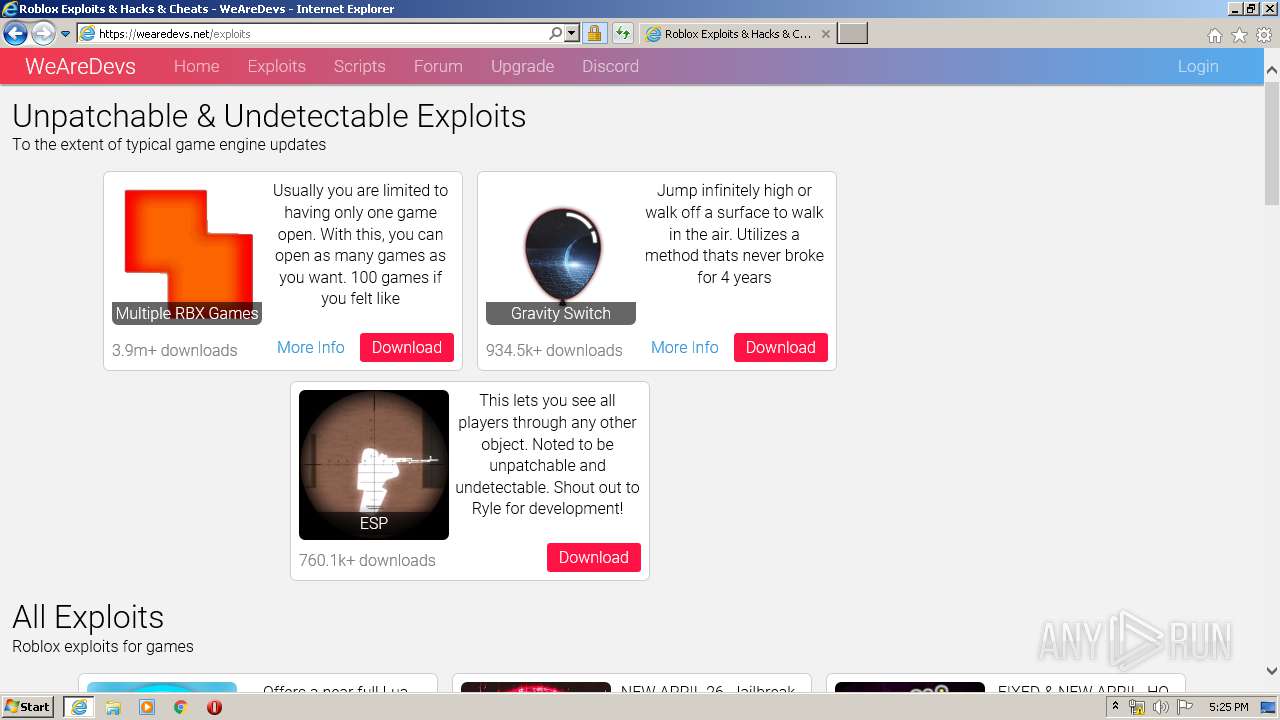
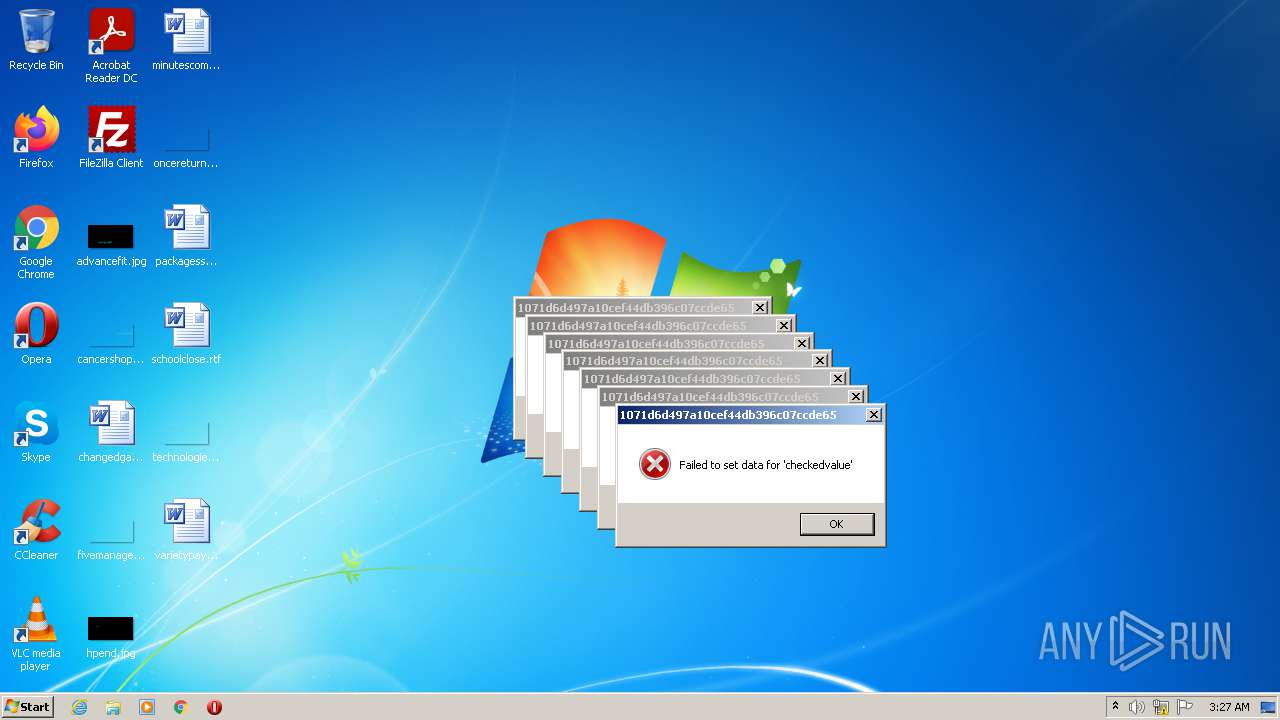
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
Krebs on Security – In-depth security news and investigation

Malware Analysis Benefits Incident Response
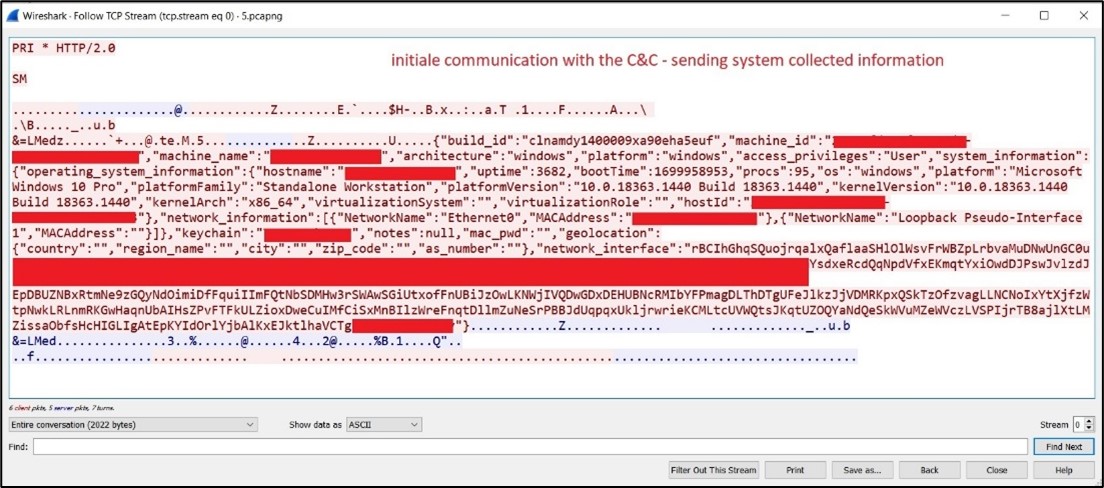
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
Most Common Malware Attacks
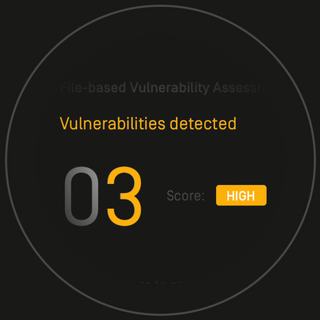
MetaDefender Cloud Advanced threat prevention and detection

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs
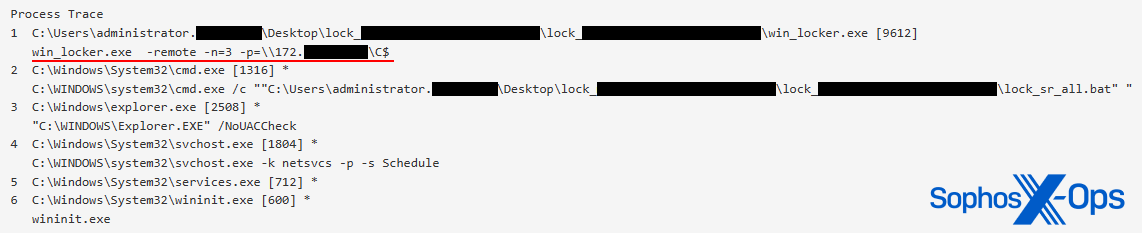
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News
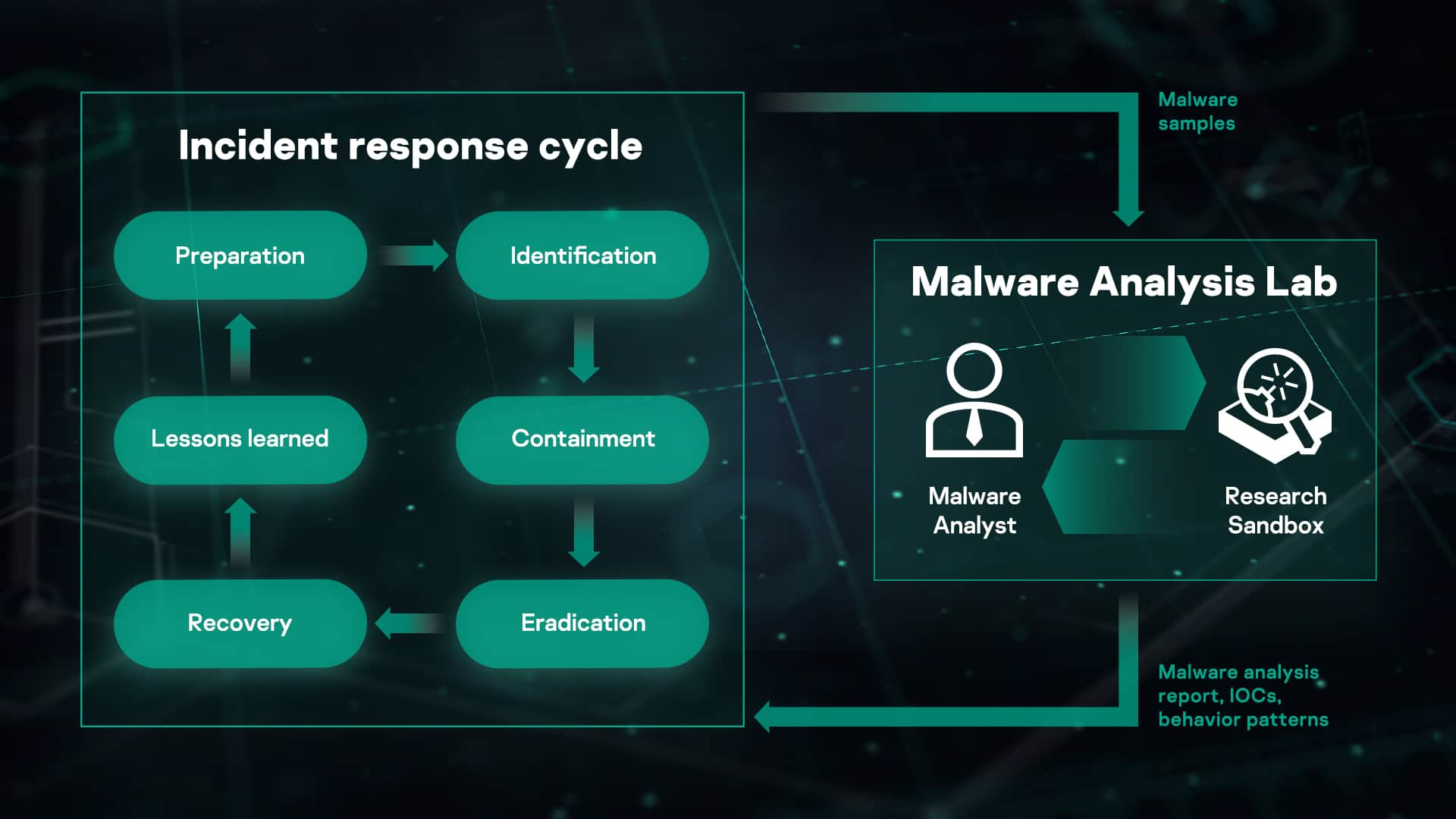
Advanced Automated Malware Analysis – Kaspersky Research Sandbox
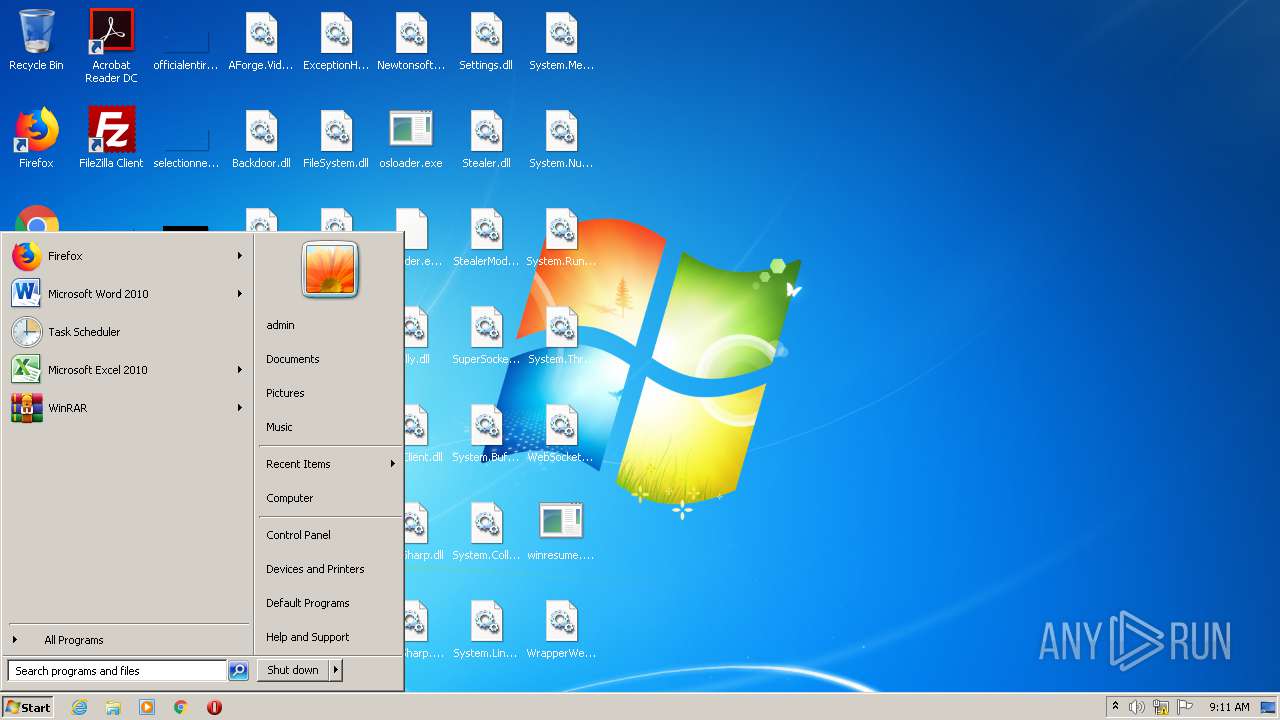
Malware analysis Release.zip Malicious activity
Recomendado para você
-
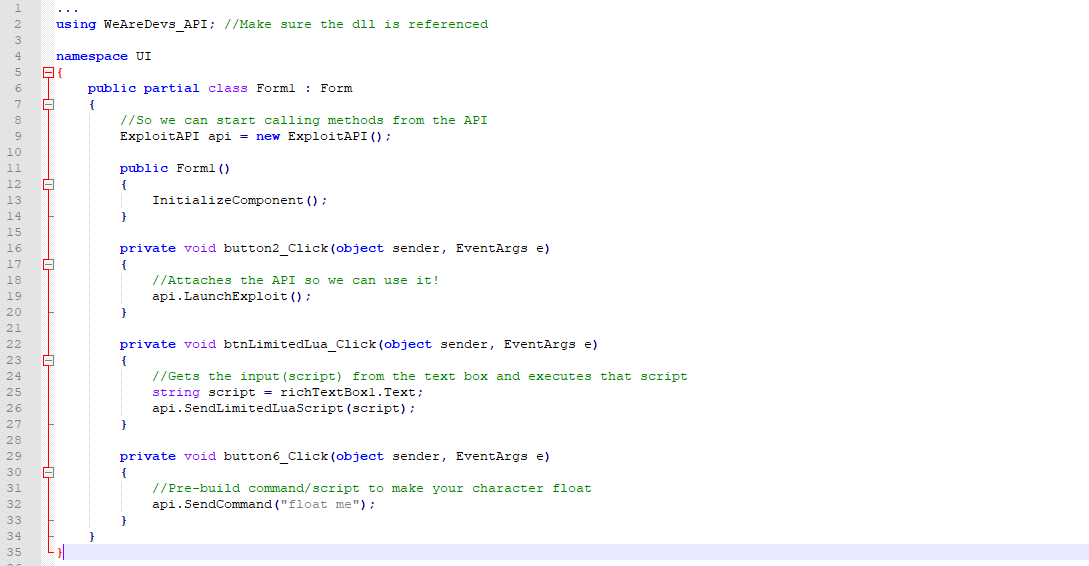 Exploit API C# Documentation & Download - WeAreDevs01 junho 2024
Exploit API C# Documentation & Download - WeAreDevs01 junho 2024 -
 Exploiter kicking everyone from the server, how to find who? - Scripting Support - Developer Forum01 junho 2024
Exploiter kicking everyone from the server, how to find who? - Scripting Support - Developer Forum01 junho 2024 -
 Roblox Executor - The Ultimate Tool for Dominating Roblox Games01 junho 2024
Roblox Executor - The Ultimate Tool for Dominating Roblox Games01 junho 2024 -
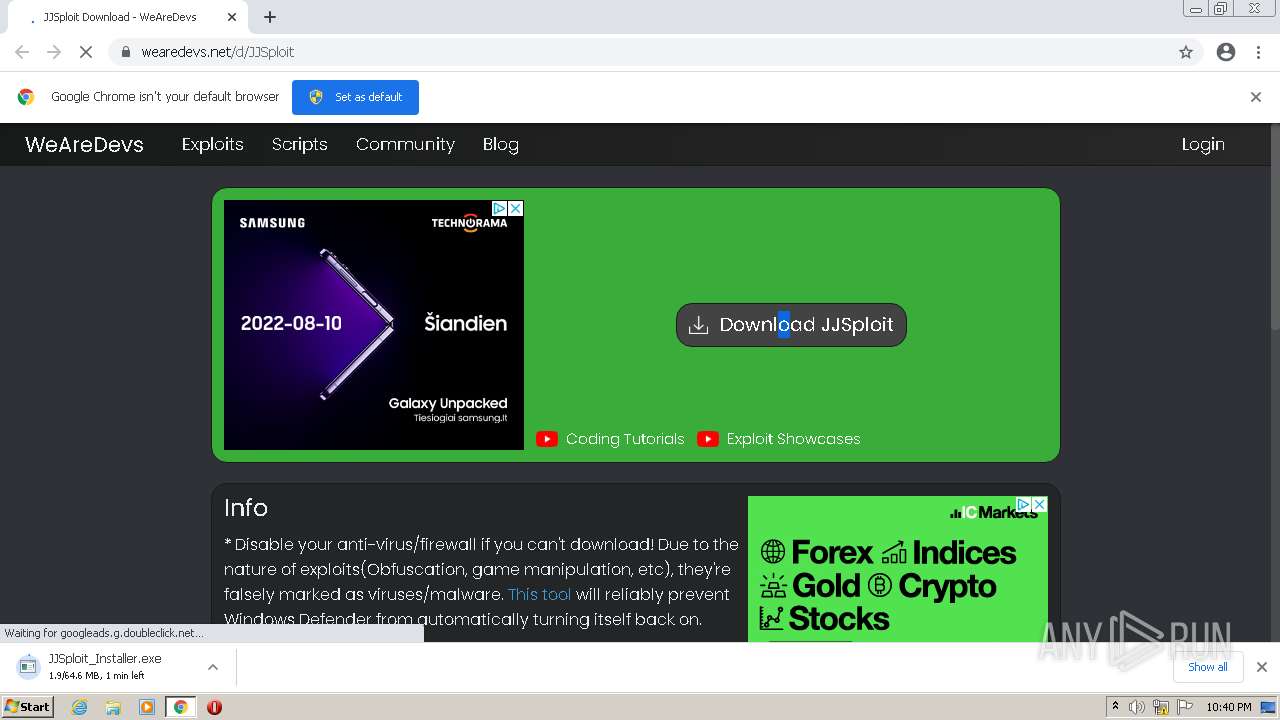 Malware analysis Malicious activity01 junho 2024
Malware analysis Malicious activity01 junho 2024 -
 🤑ROBLOX HACK TUTORIAL🤑 (GERMAN)01 junho 2024
🤑ROBLOX HACK TUTORIAL🤑 (GERMAN)01 junho 2024 -
GitHub - Professor-Puddle/Roblox-Executor: An awesome Roblox Executor that uses WeAreDevs's API. Can execute most scripts, including Eclipse Hub, and has it's own bootstrapper. Read the README file of this repository for mor01 junho 2024
-
 HOW to FIX ERROR 404 in ANY ROBLOX WEAREDEVS EXPLOIT (TUTORIAL01 junho 2024
HOW to FIX ERROR 404 in ANY ROBLOX WEAREDEVS EXPLOIT (TUTORIAL01 junho 2024 -
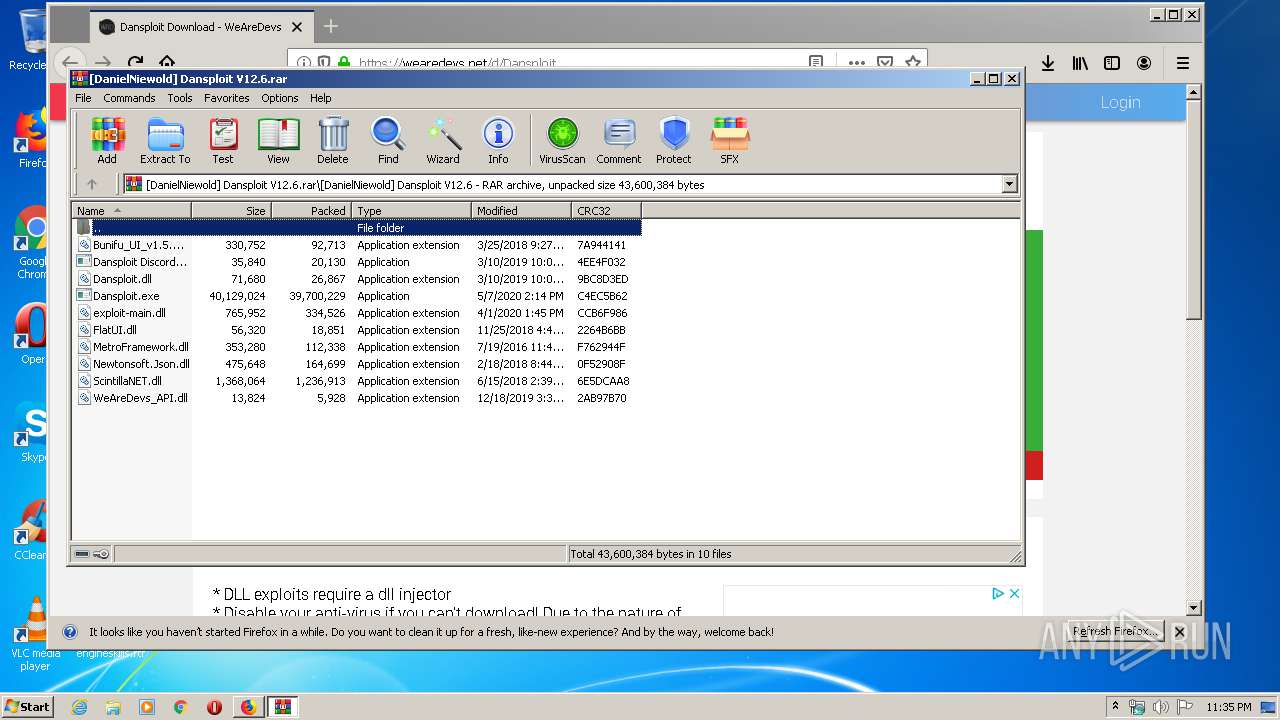 Malware analysis Malicious activity01 junho 2024
Malware analysis Malicious activity01 junho 2024 -
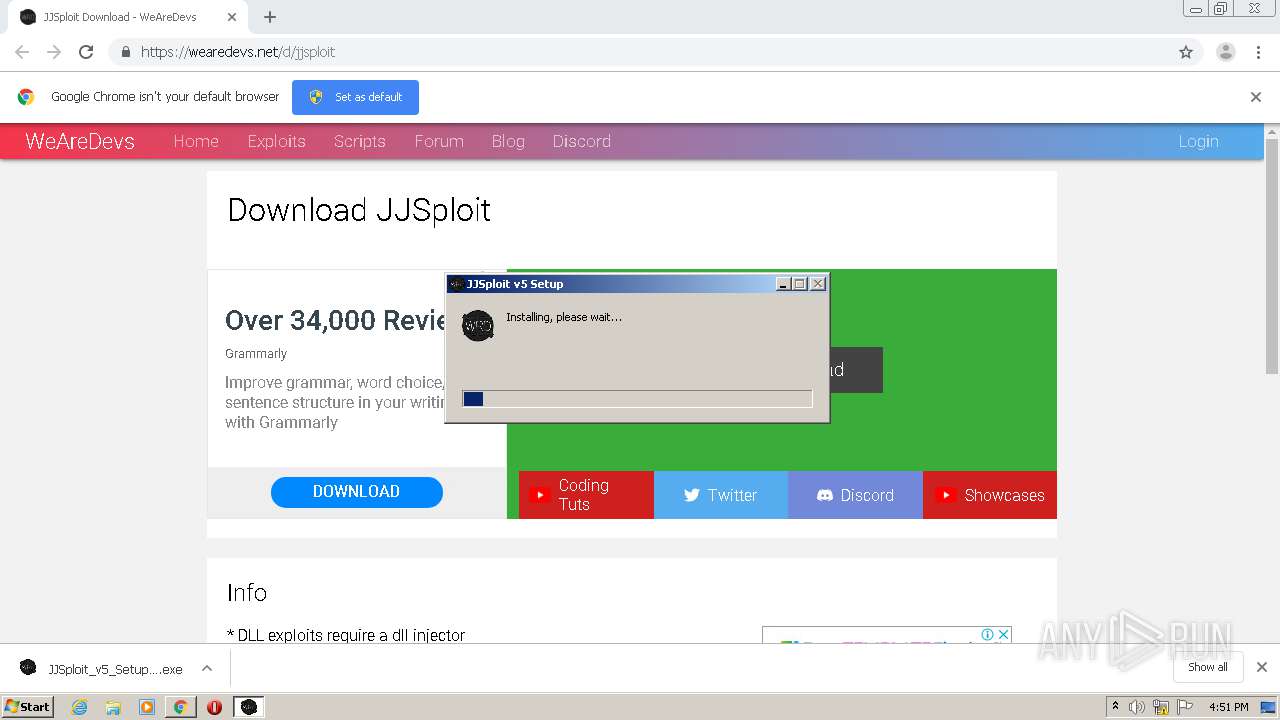 Malware analysis Malicious01 junho 2024
Malware analysis Malicious01 junho 2024 -
![Protostar v1.1 [wearedevs free exploit] [not a rat, metroskinned] - WRD Community](https://i.gyazo.com/f8da5f89fce322e5cca923ef4e0aaaaa.png) Protostar v1.1 [wearedevs free exploit] [not a rat, metroskinned] - WRD Community01 junho 2024
Protostar v1.1 [wearedevs free exploit] [not a rat, metroskinned] - WRD Community01 junho 2024
você pode gostar
-
 My Top 3 COTE Males and Females : r/ClassroomOfTheElite01 junho 2024
My Top 3 COTE Males and Females : r/ClassroomOfTheElite01 junho 2024 -
 NEW! Update In One Piece Awakening! Showcasing Ope Ope No Mi!01 junho 2024
NEW! Update In One Piece Awakening! Showcasing Ope Ope No Mi!01 junho 2024 -
Shanghaivania - Ink Sans Fight (My Take) - TurboWarp01 junho 2024
-
 Thank you #fyp #dreamybull #meme#viral#thankyou01 junho 2024
Thank you #fyp #dreamybull #meme#viral#thankyou01 junho 2024 -
 Thorfinn MBTI Personality Type: ISFP or ISFJ?01 junho 2024
Thorfinn MBTI Personality Type: ISFP or ISFJ?01 junho 2024 -
 10 Pçs Monta Partículas 87991 Peruca Para Meninos Cabelo Com Franja Oblíqua Blocos De Construção Peças Substituíveis Brinquedos Para Presente Das Crianças - Blocos Montáveis - AliExpress01 junho 2024
10 Pçs Monta Partículas 87991 Peruca Para Meninos Cabelo Com Franja Oblíqua Blocos De Construção Peças Substituíveis Brinquedos Para Presente Das Crianças - Blocos Montáveis - AliExpress01 junho 2024 -
 NPG x88188; Toby Stephens - Portrait - National Portrait Gallery01 junho 2024
NPG x88188; Toby Stephens - Portrait - National Portrait Gallery01 junho 2024 -
Title; Battlebox (2023) Genre; Action, Dram, History War Rate; 7.9 Storyline With a sudden attack by the Japanese, British…01 junho 2024
-
 Record: Tudo sobre desporto. Futebol, mercado, modalidades, resultados e classificações01 junho 2024
Record: Tudo sobre desporto. Futebol, mercado, modalidades, resultados e classificações01 junho 2024 -
 Djokovic vai à cerimônia da Bola de Ouro e abraça Messi01 junho 2024
Djokovic vai à cerimônia da Bola de Ouro e abraça Messi01 junho 2024
