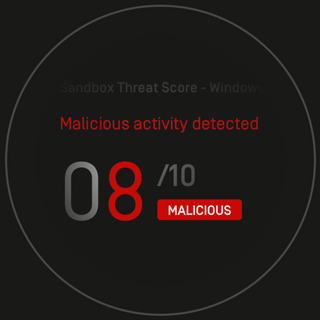
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 16 junho 2024

A detailed analysis of the Menorah malware used by APT34
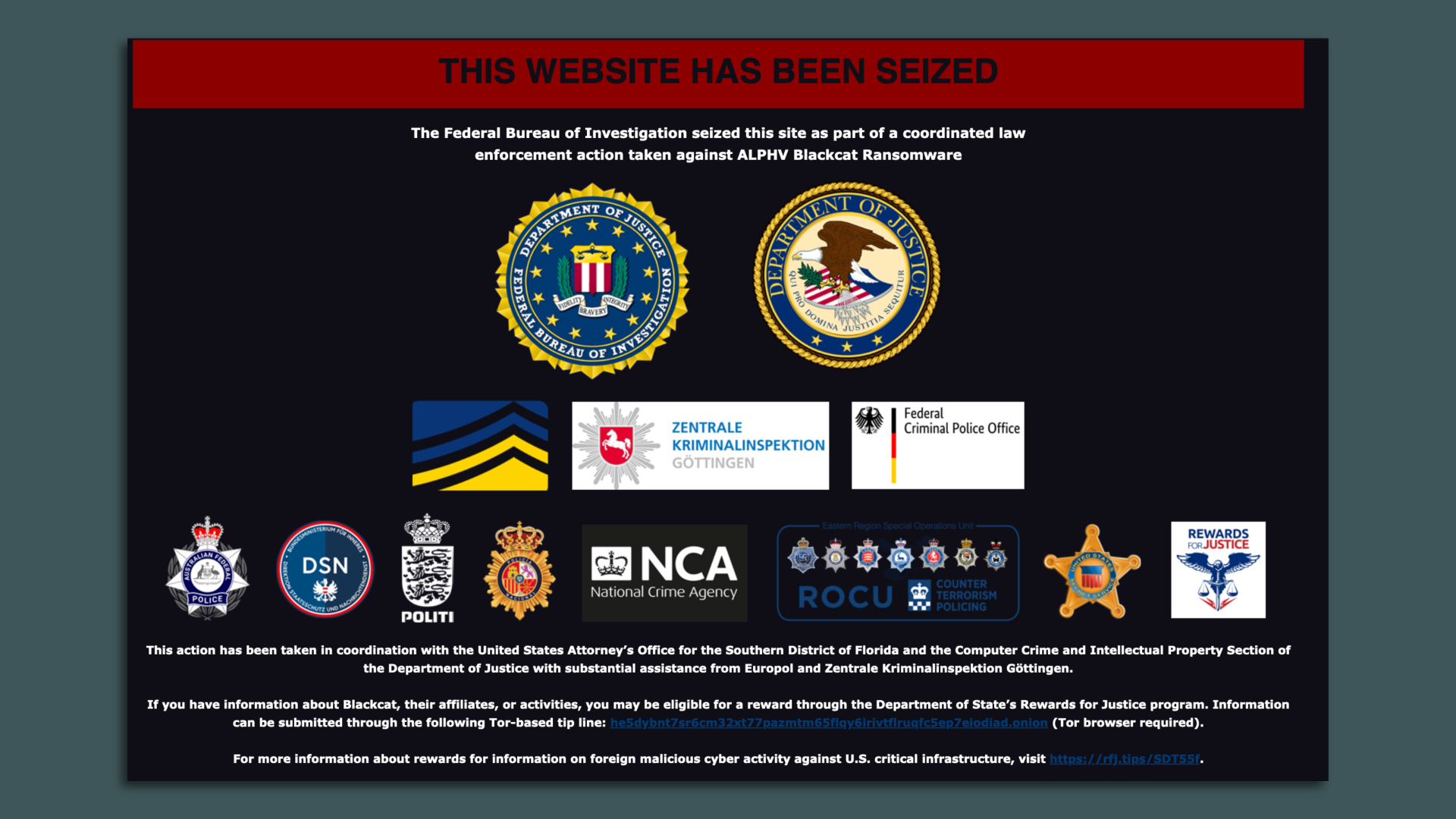
U.S. law enforcement seizes BlackCat ransomware site, distributes decryption key

Dynamic malware analysis [34]

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Malware Analysis: Protecting Your Network from Cyber Attacks

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog

Malware Analysis: Steps & Examples - CrowdStrike
MetaDefender Cloud Advanced threat prevention and detection
Recomendado para você
-
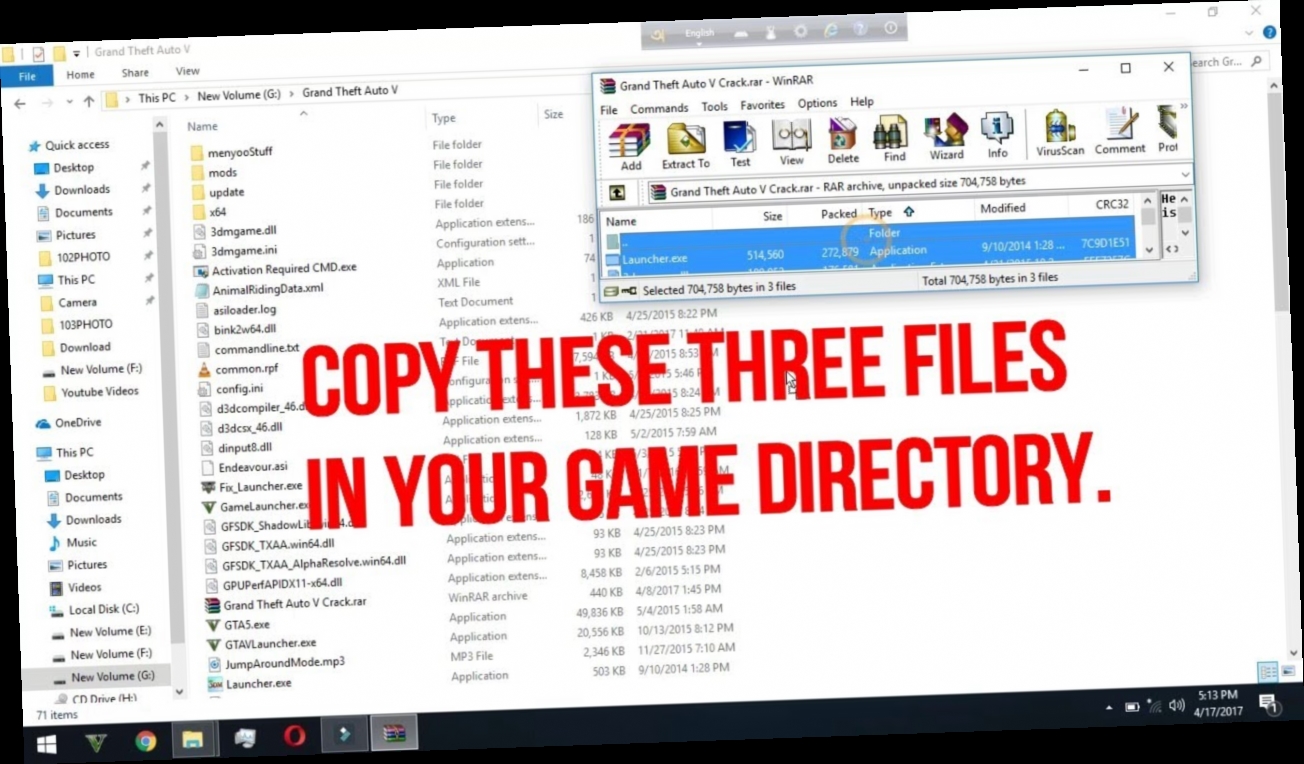
![GTA V Crack Only Download Free for PC [Reloaded] - Rihno Games](https://i0.wp.com/rihnogames.com/wp-content/uploads/2017/02/GTA-5-Free-Download.jpg?resize=350%2C200&ssl=1) GTA V Crack Only Download Free for PC [Reloaded] - Rihno Games16 junho 2024
GTA V Crack Only Download Free for PC [Reloaded] - Rihno Games16 junho 2024 -
gta v crack file download / X16 junho 2024
-
 Download Third patch (1.0.350.1) for GTA 516 junho 2024
Download Third patch (1.0.350.1) for GTA 516 junho 2024 -
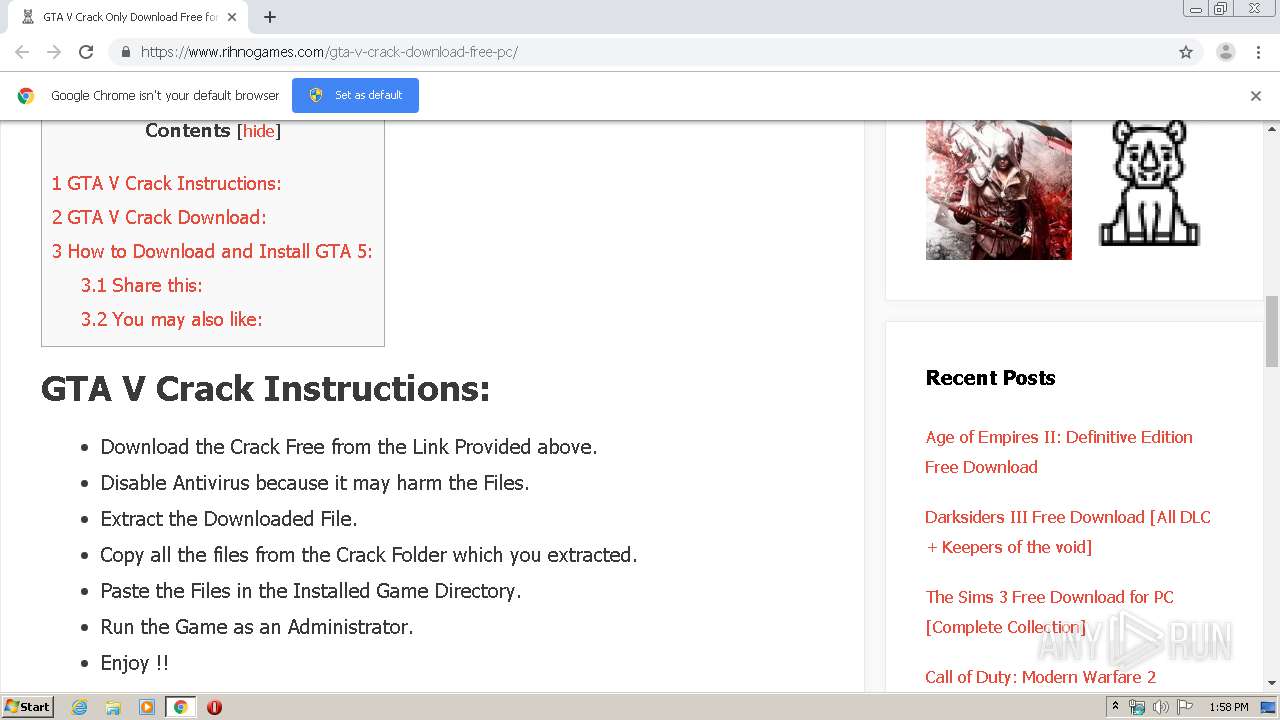
![GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)](https://i0.wp.com/activationkey.org/wp-content/uploads/2020/04/Grand-Theft-Auto-V-RockStar-500x600-1.jpg?resize=260%2C302&ssl=1) GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)16 junho 2024
GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)16 junho 2024 -
How to Download and Install GTA 5 Cracked!!!! - video Dailymotion16 junho 2024
-
 Grand Theft Auto V CPY Crack PC Free Download Torrent - CPY GAMES16 junho 2024
Grand Theft Auto V CPY Crack PC Free Download Torrent - CPY GAMES16 junho 2024 -
⬇️How To Download and install GTA 5 Crack Download Link on PC16 junho 2024
-
Instruction - How To Crack GTA IV, PDF, Utility Software16 junho 2024
-
How to download gta v on cd keys|TikTok Search16 junho 2024
-
 GTA V for PC cracked, 8 installation discs, SALE Q75 (~$10) I still remember buying pirated games in markets in my country. Many people still don't have fast internet to download torrents.16 junho 2024
GTA V for PC cracked, 8 installation discs, SALE Q75 (~$10) I still remember buying pirated games in markets in my country. Many people still don't have fast internet to download torrents.16 junho 2024
você pode gostar
-
 Jogo sushi go party devir16 junho 2024
Jogo sushi go party devir16 junho 2024 -
 What to spend event coins on : r/subwaysurfers16 junho 2024
What to spend event coins on : r/subwaysurfers16 junho 2024 -
 Pokémon Scarlet & Violet's Starter Evolutions Guide16 junho 2024
Pokémon Scarlet & Violet's Starter Evolutions Guide16 junho 2024 -
 Mettler Toledo pH Meters16 junho 2024
Mettler Toledo pH Meters16 junho 2024 -
 Moto X3M Play Online Now16 junho 2024
Moto X3M Play Online Now16 junho 2024 -
 Dragon Ball - Custom SSJ4 Gogeta Figure – Anime Toy Shop16 junho 2024
Dragon Ball - Custom SSJ4 Gogeta Figure – Anime Toy Shop16 junho 2024 -
Saruto Uchiha Uzumaki Hyuga16 junho 2024
-
 Osana Najimi Casual Dress Up Yandere Simulator by DelisaGrace896 on DeviantArt16 junho 2024
Osana Najimi Casual Dress Up Yandere Simulator by DelisaGrace896 on DeviantArt16 junho 2024 -
 🍪Little mouse making their way in the world🍪 — Day 27: FNAF Movie16 junho 2024
🍪Little mouse making their way in the world🍪 — Day 27: FNAF Movie16 junho 2024 -
 Complete Guide to the Walt Disney World Railroad - WDW Prep School16 junho 2024
Complete Guide to the Walt Disney World Railroad - WDW Prep School16 junho 2024