Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Last updated 17 junho 2024
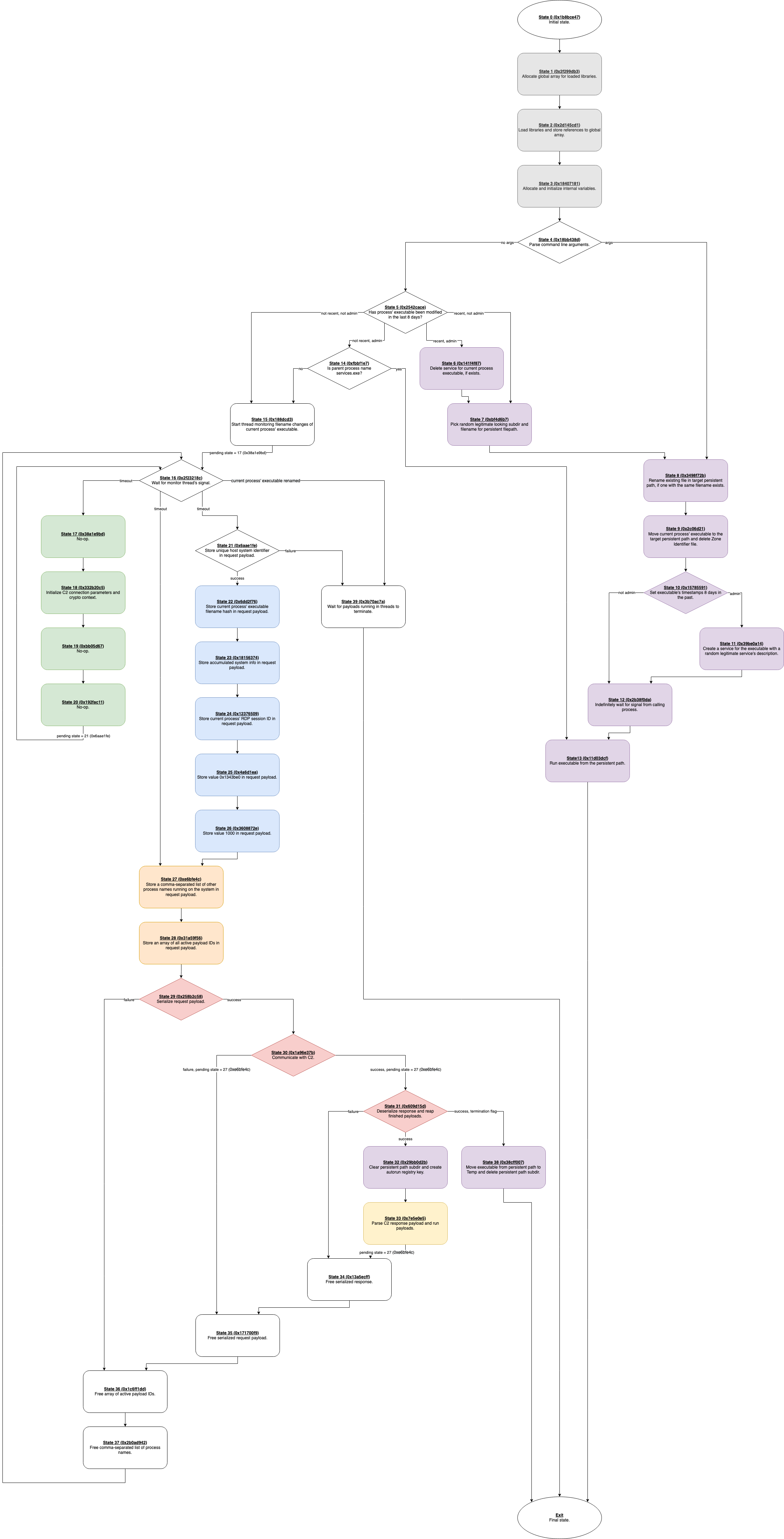
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

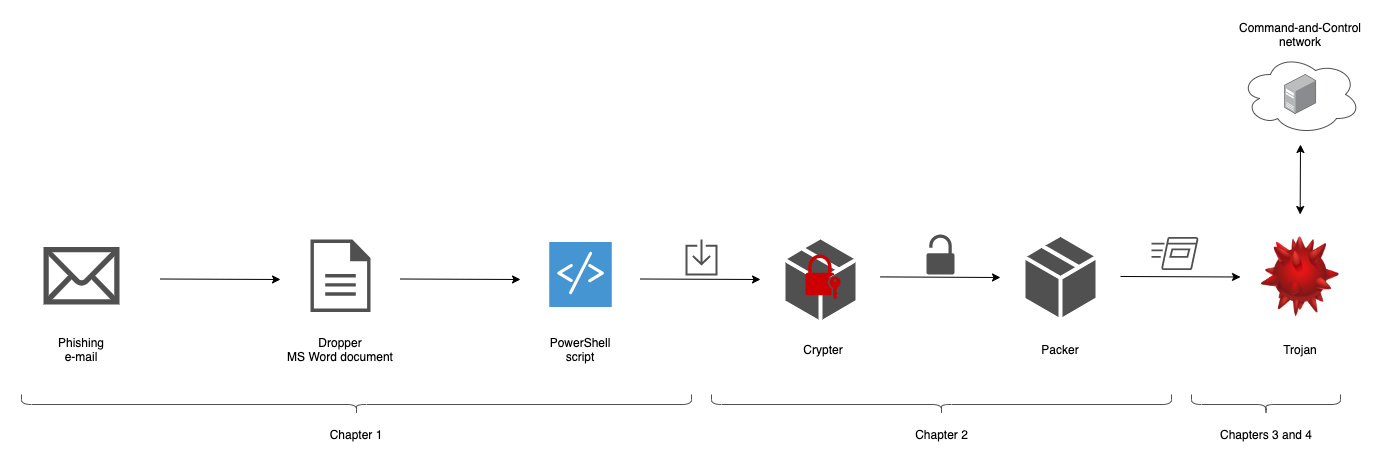
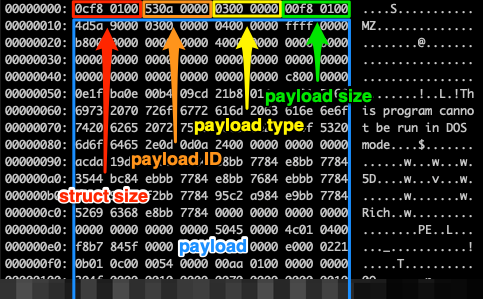
Unpacking Emotet Trojan. Emotet, in general, is a banking…, by mov eax, 27
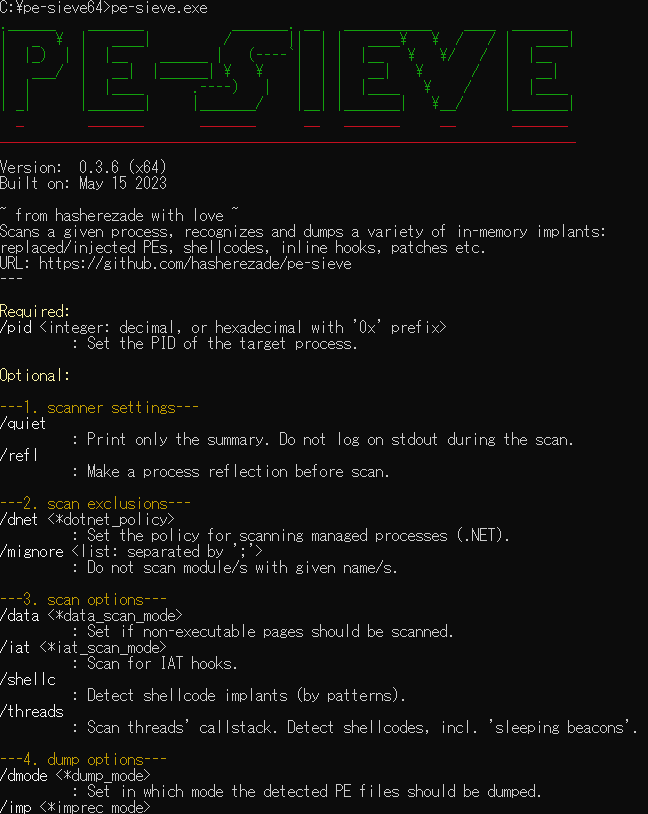
PE-sieve サイバーセキュリティ情報局
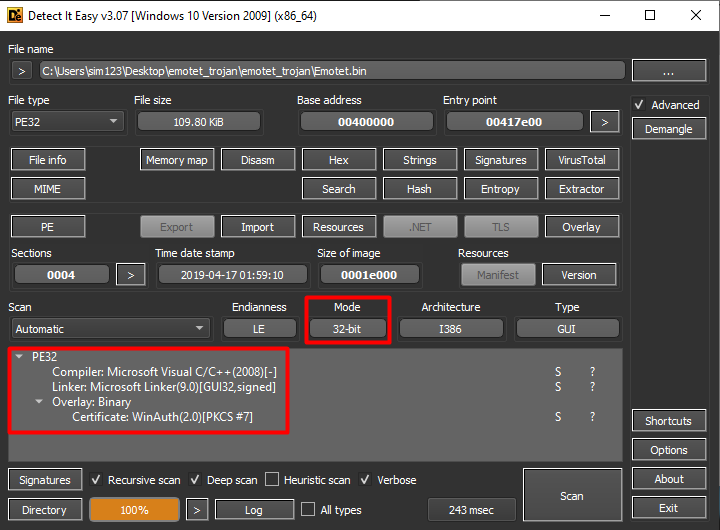
Unpacking Emotet Trojan. Emotet, in general, is a banking…, by mov eax, 27
Emotet Malware 0x01 - MalGamy
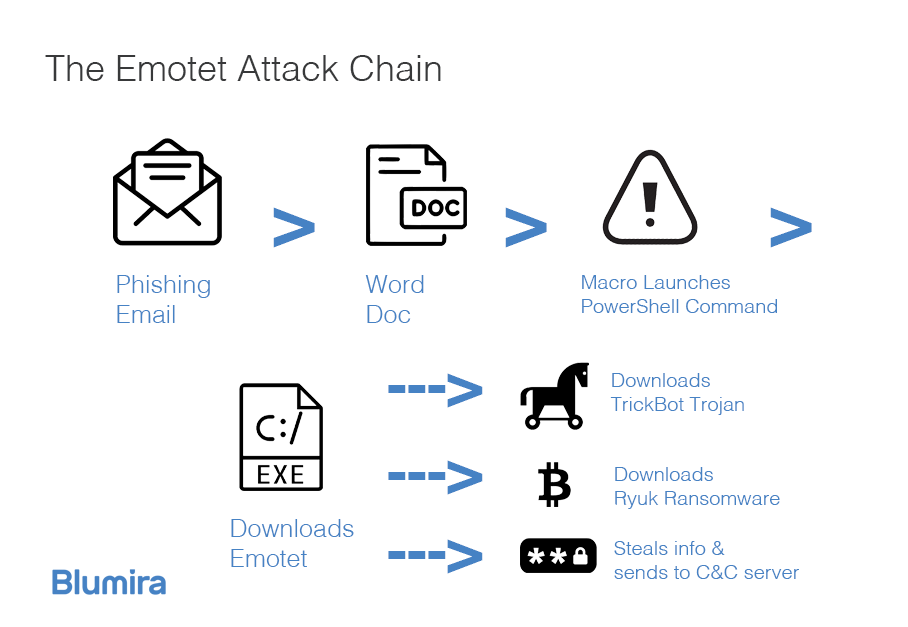
Detect and Protect Against the Return of Emotet Malware

Reverse engineering for offsec: Unpacking emotet malware., Deepanjal . posted on the topic

Reverse Engineering Emotet. (Behavior and Static Analysis), by Bruno Costa

A full reverse engineering analysis of the emotet trojan : r/netsec
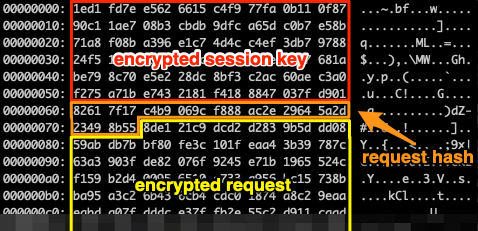
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
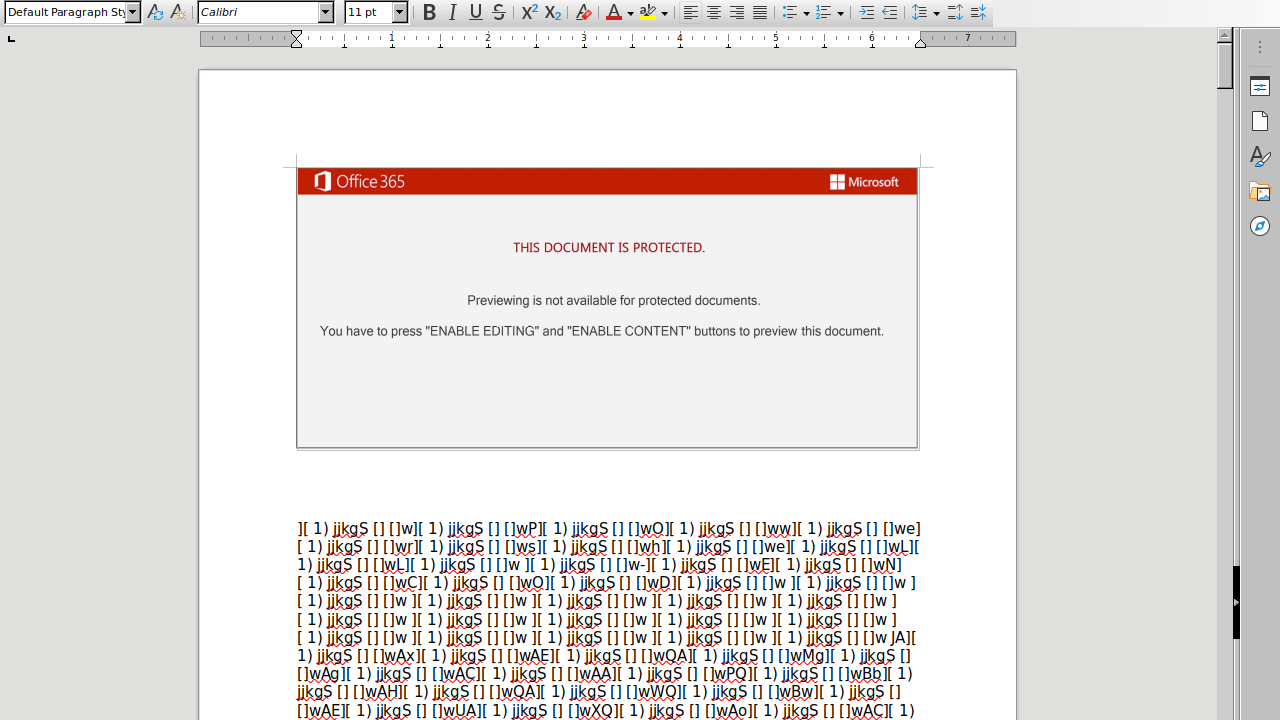
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
LearingMaterials/MalwareAnalysis.md at main · lasq88/LearingMaterials · GitHub

What is Emotet How to best protect yourself
Emotet Uses Camouflaged Malicious Macros to Avoid Antivirus Detection
Recomendado para você
-
 Terraria Starlight River Mod: Unique Bosses, Boss Rush Modes, Abilities, & How to Install17 junho 2024
Terraria Starlight River Mod: Unique Bosses, Boss Rush Modes, Abilities, & How to Install17 junho 2024 -
 How to beat all the Terraria Bosses17 junho 2024
How to beat all the Terraria Bosses17 junho 2024 -
 X 上的 NiezziQ:「Illustrated Terraria boss progression and their respective summoning methods! This was fun to make, maybe it will be useful to some new players someday. #Terraria #TerrariaJourneysEnd / X17 junho 2024
X 上的 NiezziQ:「Illustrated Terraria boss progression and their respective summoning methods! This was fun to make, maybe it will be useful to some new players someday. #Terraria #TerrariaJourneysEnd / X17 junho 2024 -
calamity boss progression|TikTok Search17 junho 2024
-
 Brain of Cthulhu in Terraria17 junho 2024
Brain of Cthulhu in Terraria17 junho 2024 -
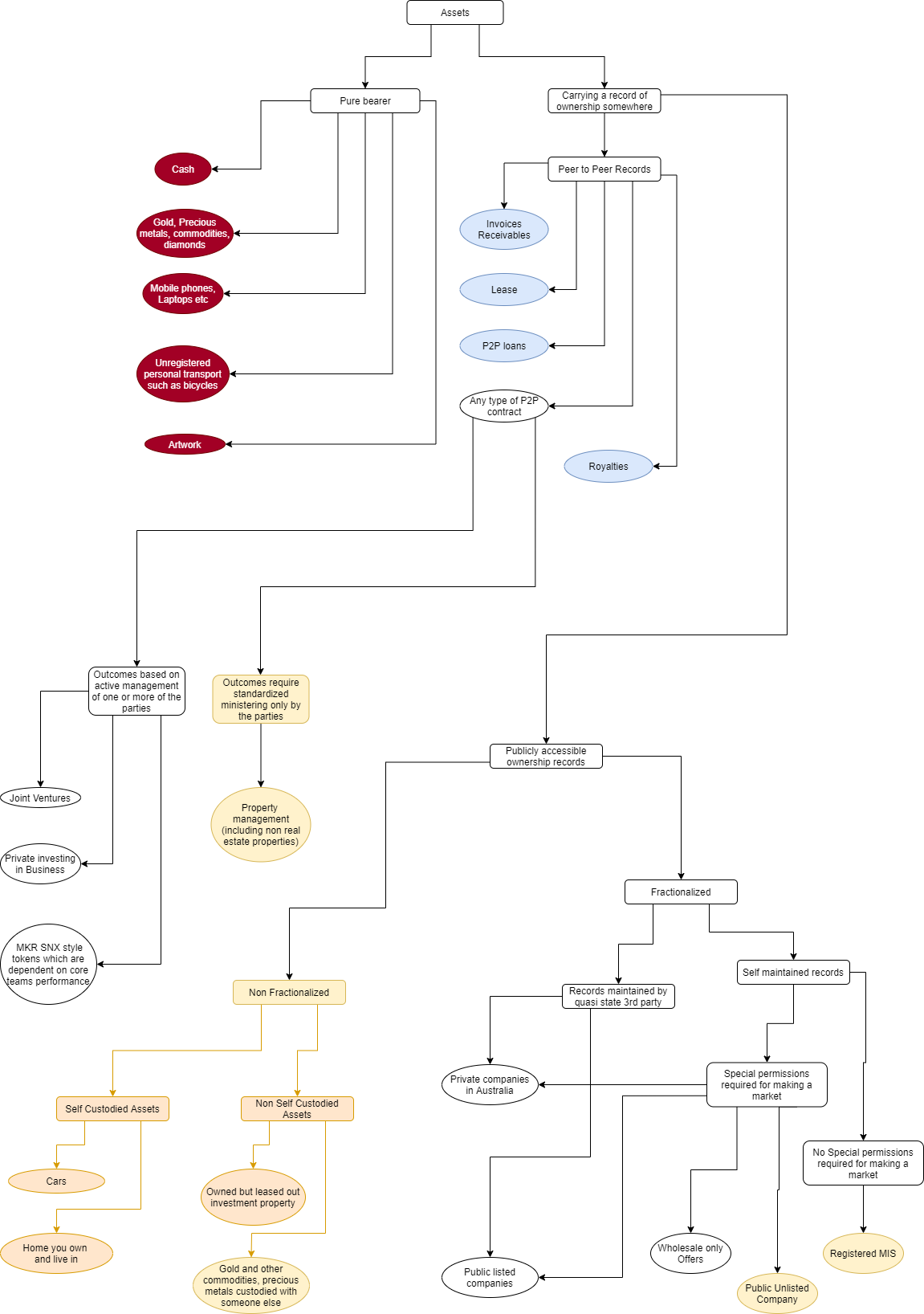 Asset classification. The dark background sections cannot be…, by Moresh Kokane, Konkrete17 junho 2024
Asset classification. The dark background sections cannot be…, by Moresh Kokane, Konkrete17 junho 2024 -
 Terraria 1.4 Master Mode Boss Progression Guide - SteamAH17 junho 2024
Terraria 1.4 Master Mode Boss Progression Guide - SteamAH17 junho 2024 -
Steam Community :: Guide :: FULL Melee Class Setup Guide For Terraria 1.4 (All Modes)17 junho 2024
-
Terraria's BEST Pre-Boss Melee Progression!!! 😜 #terraria #game #stea, terraria17 junho 2024
-
.jpg) Terraria: Moon Lord Boss Guide17 junho 2024
Terraria: Moon Lord Boss Guide17 junho 2024
você pode gostar
-
 BOLO DELICADO PARA ANIVERSÁRIO DA PROFESSORA :: Maryazinha Doces17 junho 2024
BOLO DELICADO PARA ANIVERSÁRIO DA PROFESSORA :: Maryazinha Doces17 junho 2024 -
 JOGO MINECRAFT EDITION ORIGINAL ( XBOX 360) - Desapegos de Roupas17 junho 2024
JOGO MINECRAFT EDITION ORIGINAL ( XBOX 360) - Desapegos de Roupas17 junho 2024 -
 Los pokémon fantasma son pokémon que han muerto?17 junho 2024
Los pokémon fantasma son pokémon que han muerto?17 junho 2024 -
 Desapego Games - Roblox > Conta antiga do roblox com mais de 4000 robux gastos e histórico em vários jogos17 junho 2024
Desapego Games - Roblox > Conta antiga do roblox com mais de 4000 robux gastos e histórico em vários jogos17 junho 2024 -
 Announcement: Call of Duty: Modern Warfare III Campaign Details17 junho 2024
Announcement: Call of Duty: Modern Warfare III Campaign Details17 junho 2024 -
Hajime no Ippo L.A. - Manga de boxeo, hajime no ippo anunciara una gran noticia en las próxima revista semanal shonen jump el 23 de junio Puede ser dos cosas que se17 junho 2024
-
 Pokemon GO: How to Get Solgaleo and Lunala17 junho 2024
Pokemon GO: How to Get Solgaleo and Lunala17 junho 2024 -
Given, Dublapédia17 junho 2024
-
![Gifs png [Welcome]](http://pa1.aminoapps.com/6824/7942bf84c8ee4a625ebfa745997917d6bceb011c_00.gif) Gifs png [Welcome]17 junho 2024
Gifs png [Welcome]17 junho 2024 -
 20 Cm De Desenho Animado Fofo Kuromi Brinquedo De Pelúcia Kawaii17 junho 2024
20 Cm De Desenho Animado Fofo Kuromi Brinquedo De Pelúcia Kawaii17 junho 2024




