File:SUPI-SUCI transformation.png - Wikimedia Commons
Por um escritor misterioso
Last updated 02 junho 2024


File:Transducin.png - Wikimedia Commons
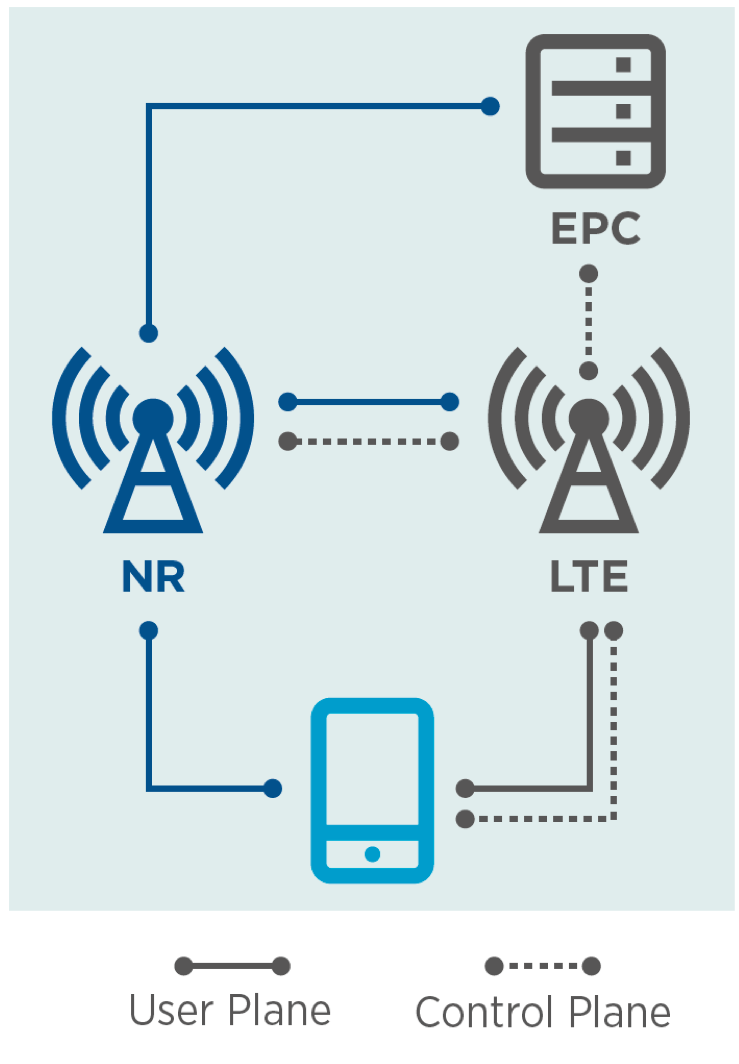
GSMA Securing the 5G Era - Security

PDF) Renata Tatomir_Coordinating Editor_Proceedings of the East-West Dialogue International Conference Second Edition Hyperion University Bucharest, June 7, 2019 (published 2020)
Within-Case Qualitative Analysis
ECIES in 5G Core: SUPI to SUCI Conversion, by Aditya Koranga
ECIES in 5G Core: SUPI to SUCI Conversion, by Aditya Koranga

Have you or someone you know stepped away from the

NationStates • View topic - World Cup 94 [roleplays]
GitHub - mitshell/CryptoMobile: Cryptography for mobile network - C implementation and Python bindings

NationStates • View topic - World Cup 94 [roleplays]

AES E-Library » Complete Journal: Volume 38 Issue 6
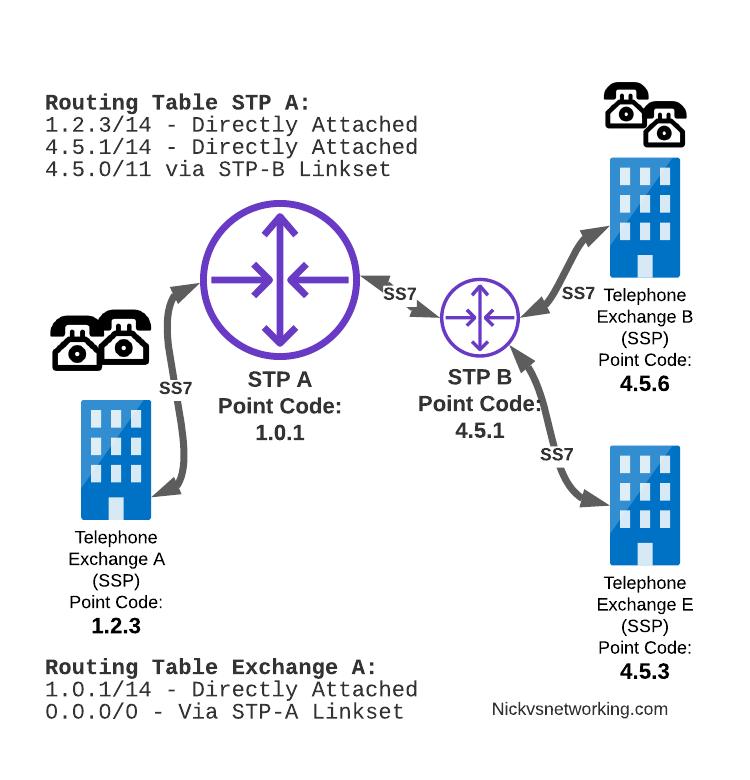
GSM Nick vs Networking
Recomendado para você
-
Luis Paulo Supi player profile - ChessBase Players02 junho 2024
-
 Luis Paulo Supi é o Campeão Brasileiro de 2020 - Xadrez Forte02 junho 2024
Luis Paulo Supi é o Campeão Brasileiro de 2020 - Xadrez Forte02 junho 2024 -
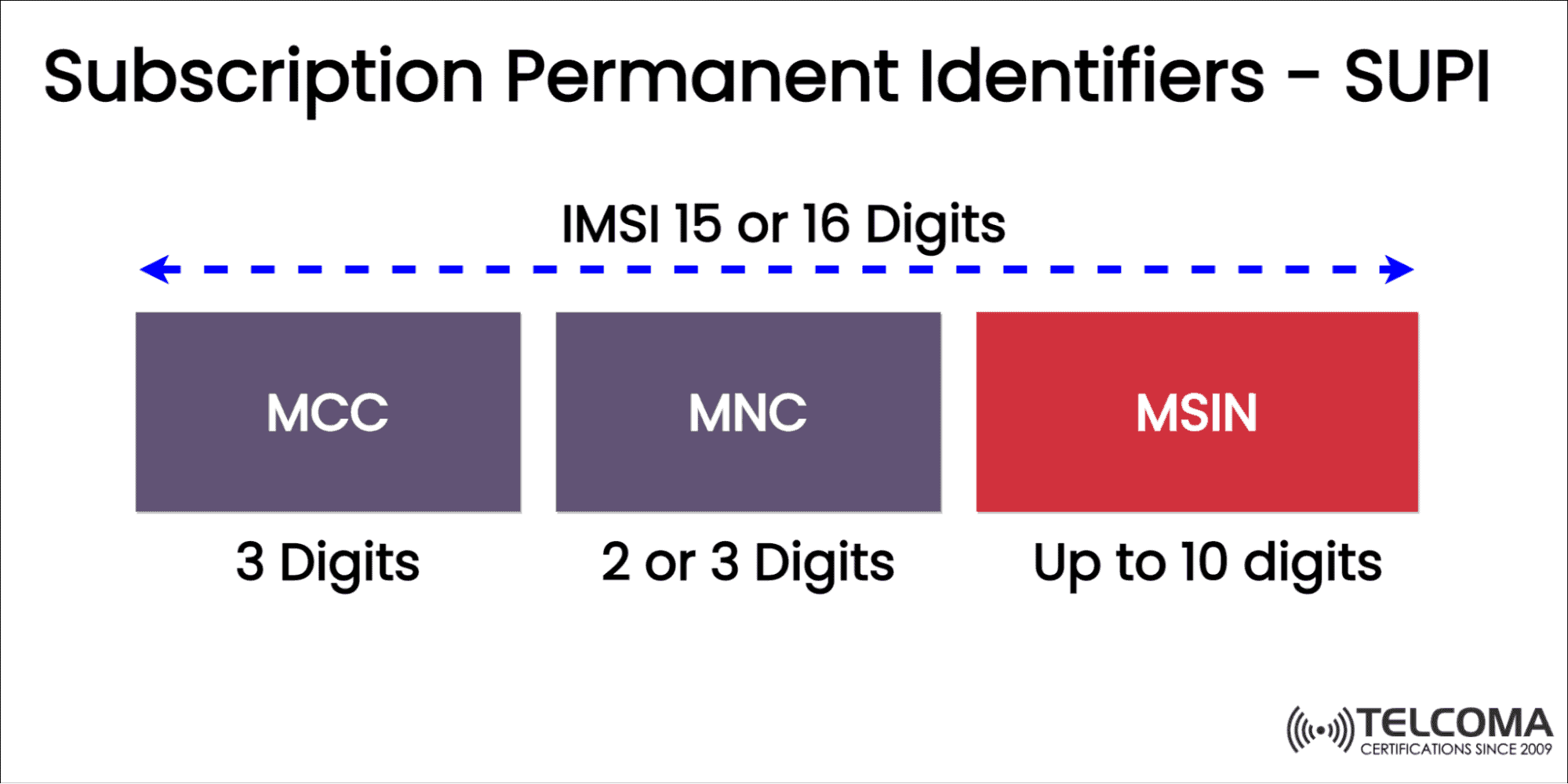
5G Identifiers SUPI, SUCI, GUTI, GPSI, PEI , AMF, DNN - TELCOMA02 junho 2024
-
 What about that time when Hikaru (falsely?) accused GM Supi of cheating? 👀 : r/chess02 junho 2024
What about that time when Hikaru (falsely?) accused GM Supi of cheating? 👀 : r/chess02 junho 2024 -
Supi02 junho 2024
-
 Cooking with Supi: Wonton Two Ways!02 junho 2024
Cooking with Supi: Wonton Two Ways!02 junho 2024 -
 SUPI' – GOS™ Sneakers02 junho 2024
SUPI' – GOS™ Sneakers02 junho 2024 -
 Supi Prach-Umpai - Thailand Travel Specialist02 junho 2024
Supi Prach-Umpai - Thailand Travel Specialist02 junho 2024 -
 Supi and Pampy behind the scenes by botsdot on DeviantArt02 junho 2024
Supi and Pampy behind the scenes by botsdot on DeviantArt02 junho 2024 -
 Clearsale Masters e Masters Feminino 2021: Finais - Terao e Supi campeões02 junho 2024
Clearsale Masters e Masters Feminino 2021: Finais - Terao e Supi campeões02 junho 2024
você pode gostar
-
Gol Bola Rebaixado - Only Cars02 junho 2024
-
 Pin on unblocked games 77 at school02 junho 2024
Pin on unblocked games 77 at school02 junho 2024 -
 DVD - Os Cavaleiros do Zodíaco - Ômega Vol. 202 junho 2024
DVD - Os Cavaleiros do Zodíaco - Ômega Vol. 202 junho 2024 -
How To Draw Anime: Beast Gohan! - Step By Step Tutorial!, Yair Sasson Art02 junho 2024
-
 Carro Super Conversível Para Barbie Pink Grande 60 Cm Líder02 junho 2024
Carro Super Conversível Para Barbie Pink Grande 60 Cm Líder02 junho 2024 -
 funk eu acredito que minha hora vai chegar02 junho 2024
funk eu acredito que minha hora vai chegar02 junho 2024 -
 Armored Mewtwo in Raid Battles - Leek Duck02 junho 2024
Armored Mewtwo in Raid Battles - Leek Duck02 junho 2024 -
 2ª Temporada de 'Jujutsu Kaisen' chegará à Crunchyroll - Mangekyou Blog02 junho 2024
2ª Temporada de 'Jujutsu Kaisen' chegará à Crunchyroll - Mangekyou Blog02 junho 2024 -
 Cassandra Clare — aegisdea: Here's my take on Camille Belcourt~ I02 junho 2024
Cassandra Clare — aegisdea: Here's my take on Camille Belcourt~ I02 junho 2024 -
 Nuno Gomes, Ronaldo e mais 9 craques portugueses que usaram fitinha02 junho 2024
Nuno Gomes, Ronaldo e mais 9 craques portugueses que usaram fitinha02 junho 2024