Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Por um escritor misterioso
Last updated 10 junho 2024

In February we saw a resurgence of Ursnif (also known as Gozi), a credential-stealing Trojan. Learn how Ursnif bypasses an attack surface reduction rule.
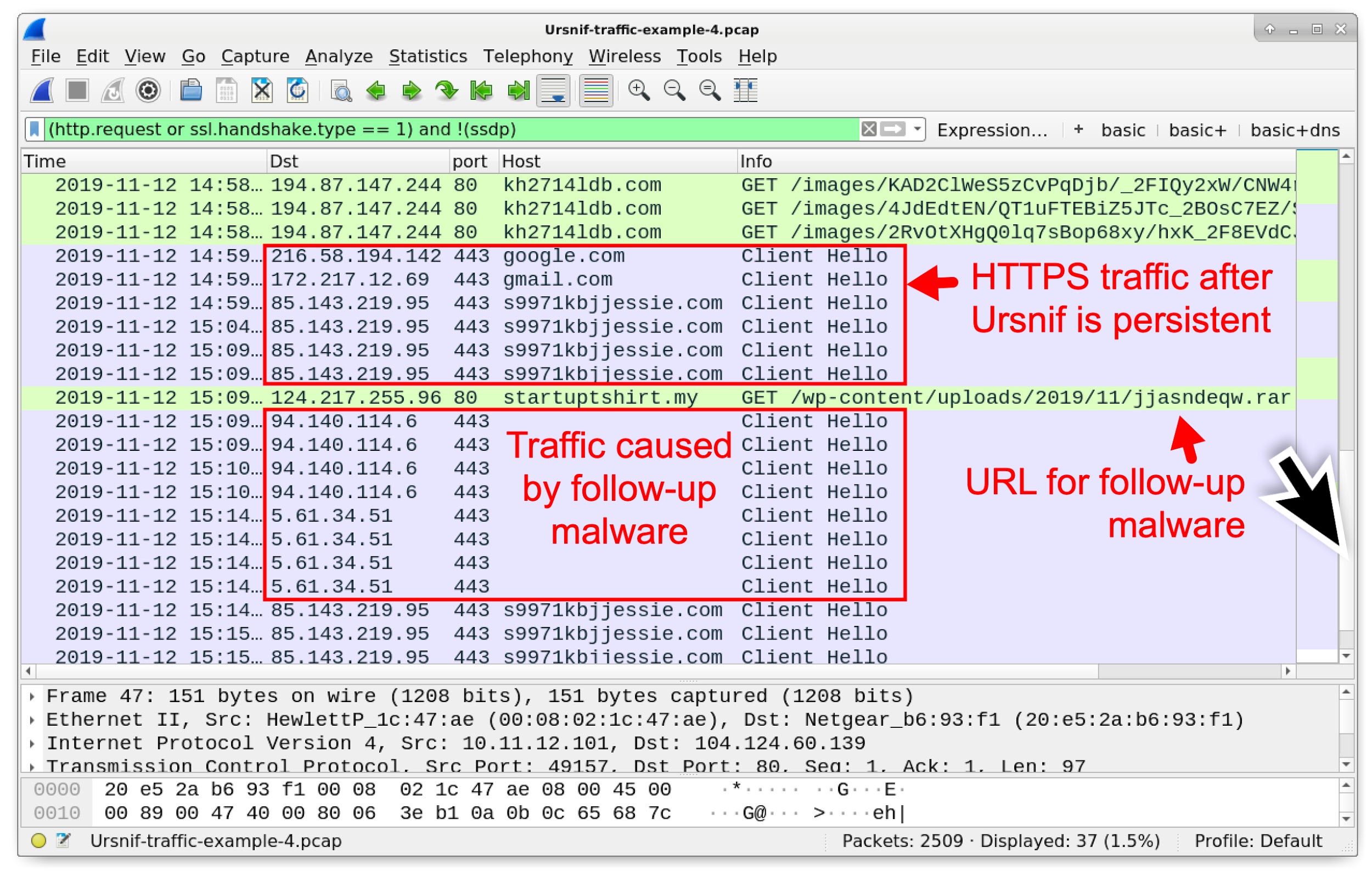
Wireshark Tutorial: Examining Ursnif Infections
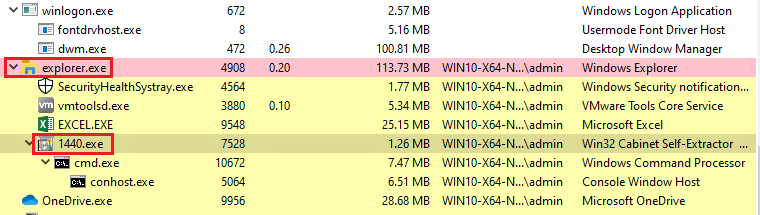
Ursnif Malware Banks on News Events for Phishing Attacks
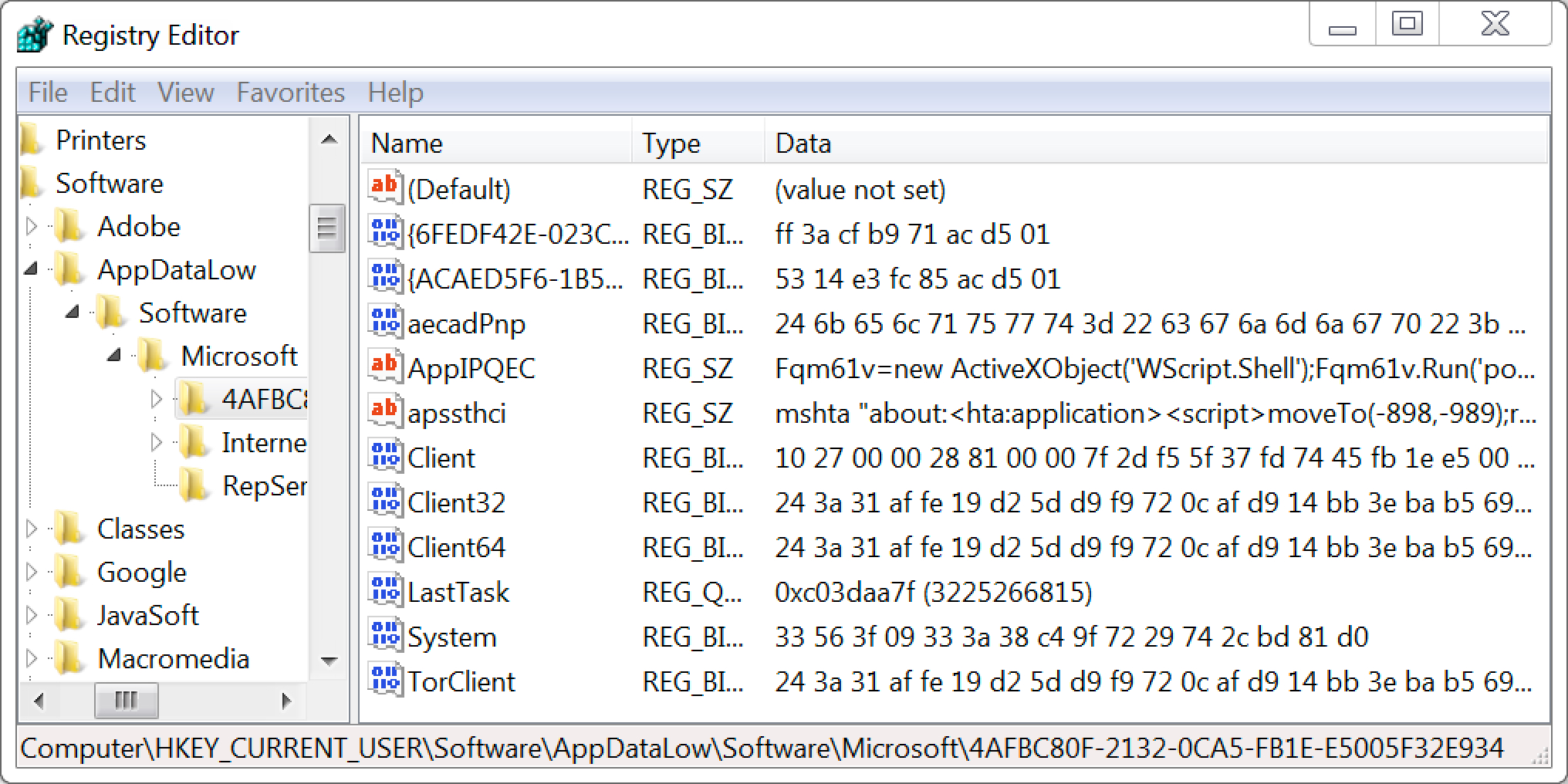
Wireshark Tutorial: Examining Ursnif Infections
Gozi: The Malware with a Thousand Faces - Check Point Research
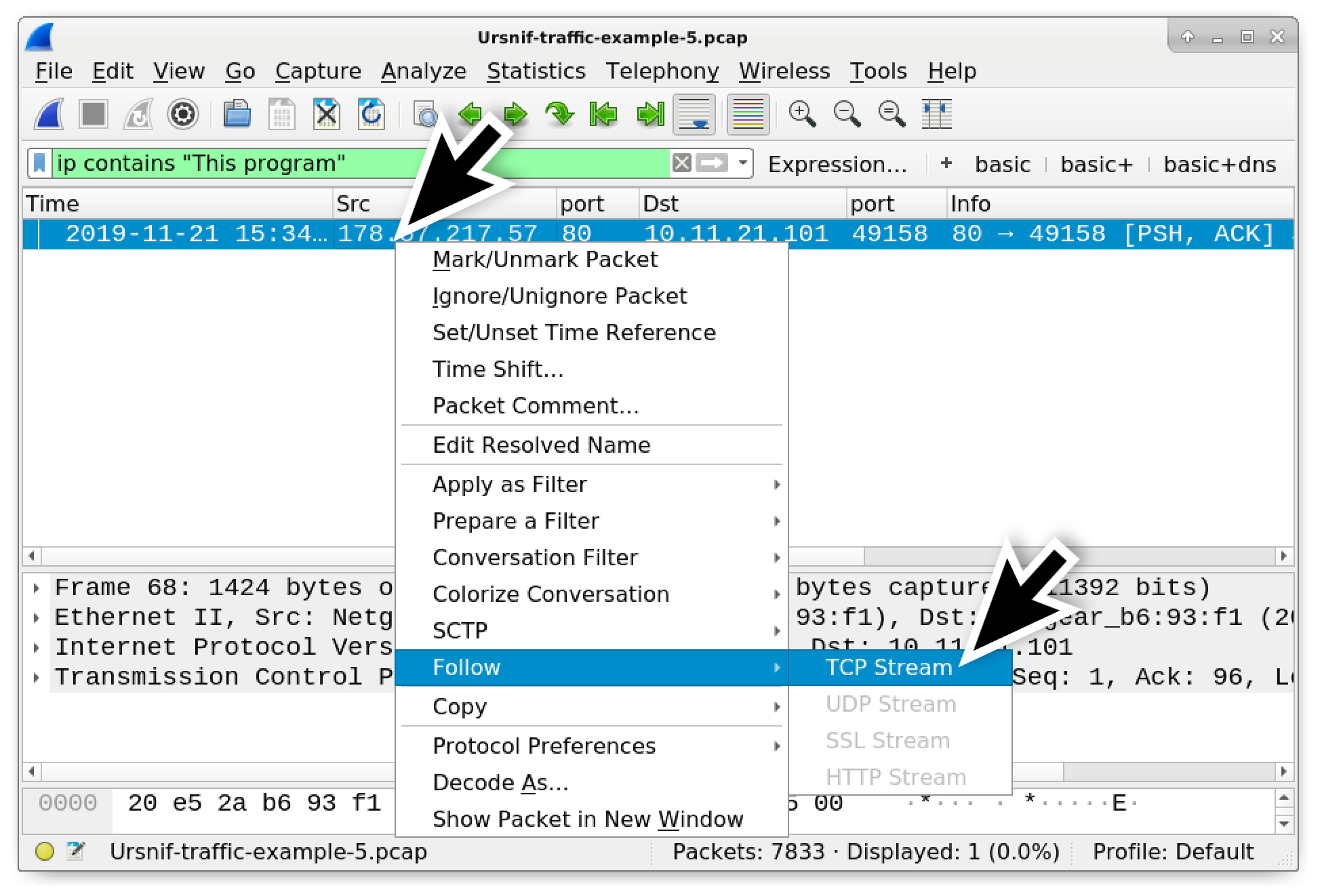
Wireshark Tutorial: Examining Ursnif Infections
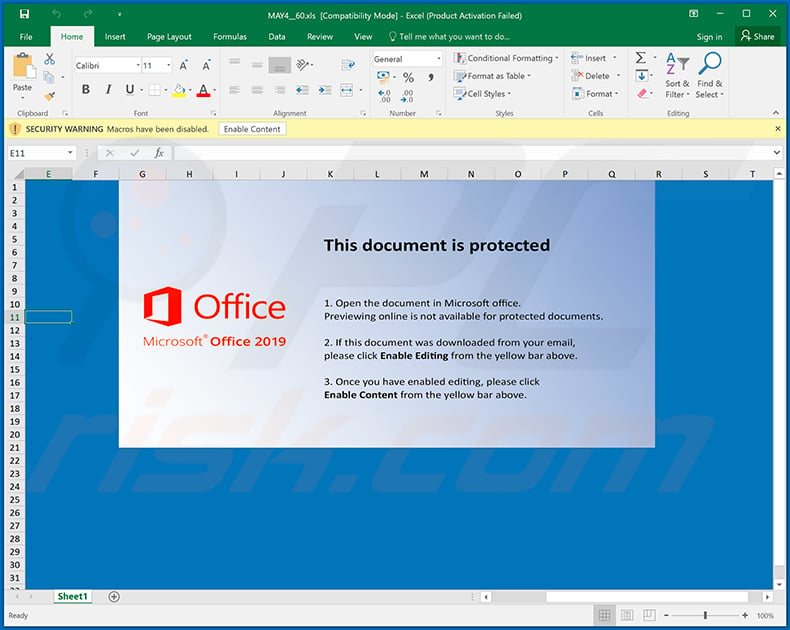
Ursnif Trojan - Malware removal instructions (updated)

Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Ursnif malware switches from bank account theft to initial access
Ursnif Trojan - Malware removal instructions (updated)
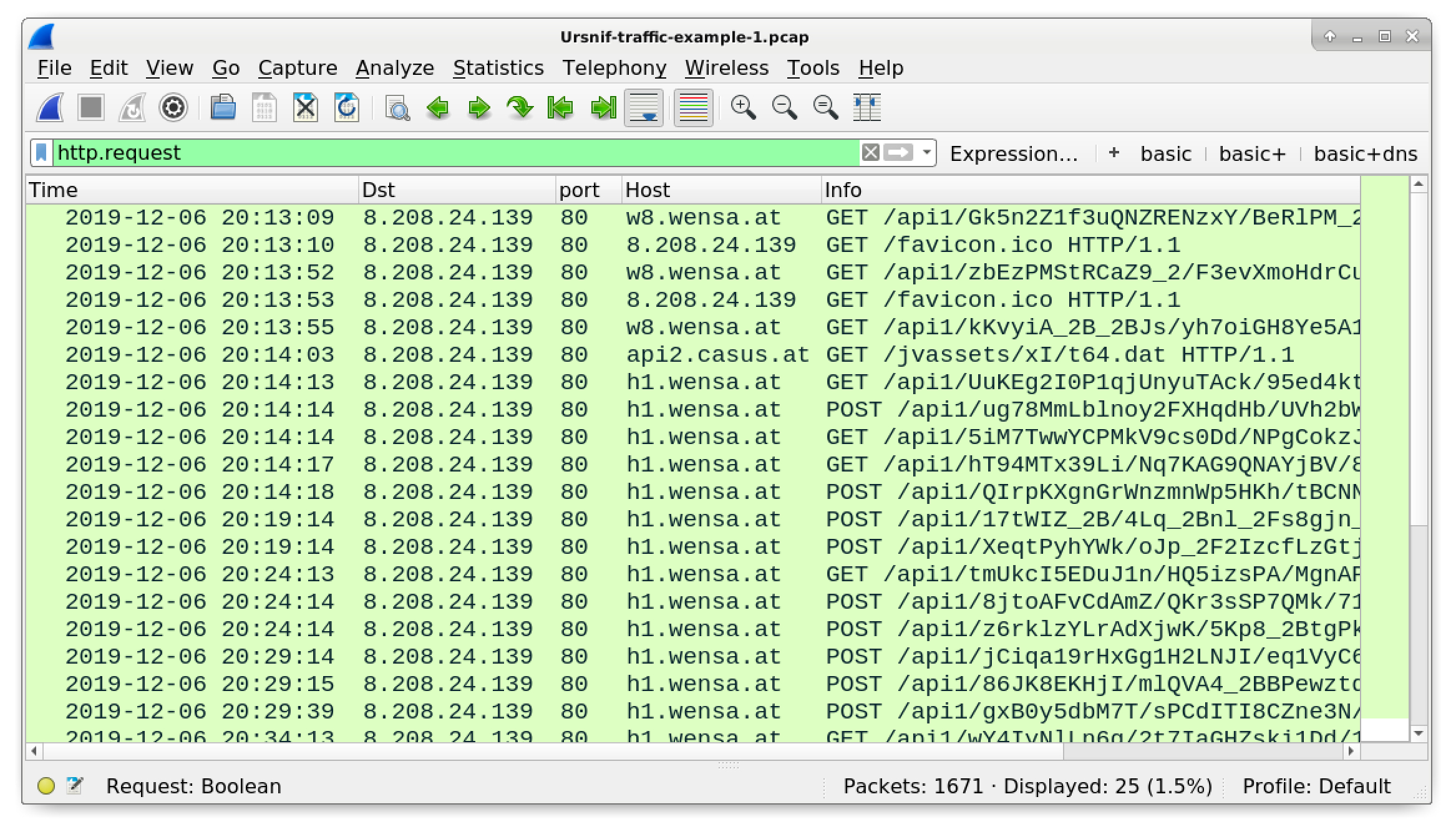
Wireshark Tutorial: Examining Ursnif Infections
Malware Analysis — Gozi/Ursnif Downloader, by ka1d0
Recomendado para você
-
 Evade synonyms - 2 269 Words and Phrases for Evade10 junho 2024
Evade synonyms - 2 269 Words and Phrases for Evade10 junho 2024 -
 Evades.io 🕹️ Play Now on GamePix10 junho 2024
Evades.io 🕹️ Play Now on GamePix10 junho 2024 -
 Hiding in Plain Sight: How HIV Evades Innate Immune Responses: Cell10 junho 2024
Hiding in Plain Sight: How HIV Evades Innate Immune Responses: Cell10 junho 2024 -
 Fox Evades10 junho 2024
Fox Evades10 junho 2024 -
 Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud10 junho 2024
Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud10 junho 2024 -
Why full 'network effect' evades Europe's start-ups10 junho 2024
-
 Good Pretty Sharp Intellect Evades The Pursuer Enola Holmes Funny Acrylic Print by Inny Shop - Pixels10 junho 2024
Good Pretty Sharp Intellect Evades The Pursuer Enola Holmes Funny Acrylic Print by Inny Shop - Pixels10 junho 2024 -
 She evades me once again I hope I can become a Dehya haver soon :( : r/Dehyamains10 junho 2024
She evades me once again I hope I can become a Dehya haver soon :( : r/Dehyamains10 junho 2024 -
 Retraining a Horse that Evades Contact - Strides for Success10 junho 2024
Retraining a Horse that Evades Contact - Strides for Success10 junho 2024 -
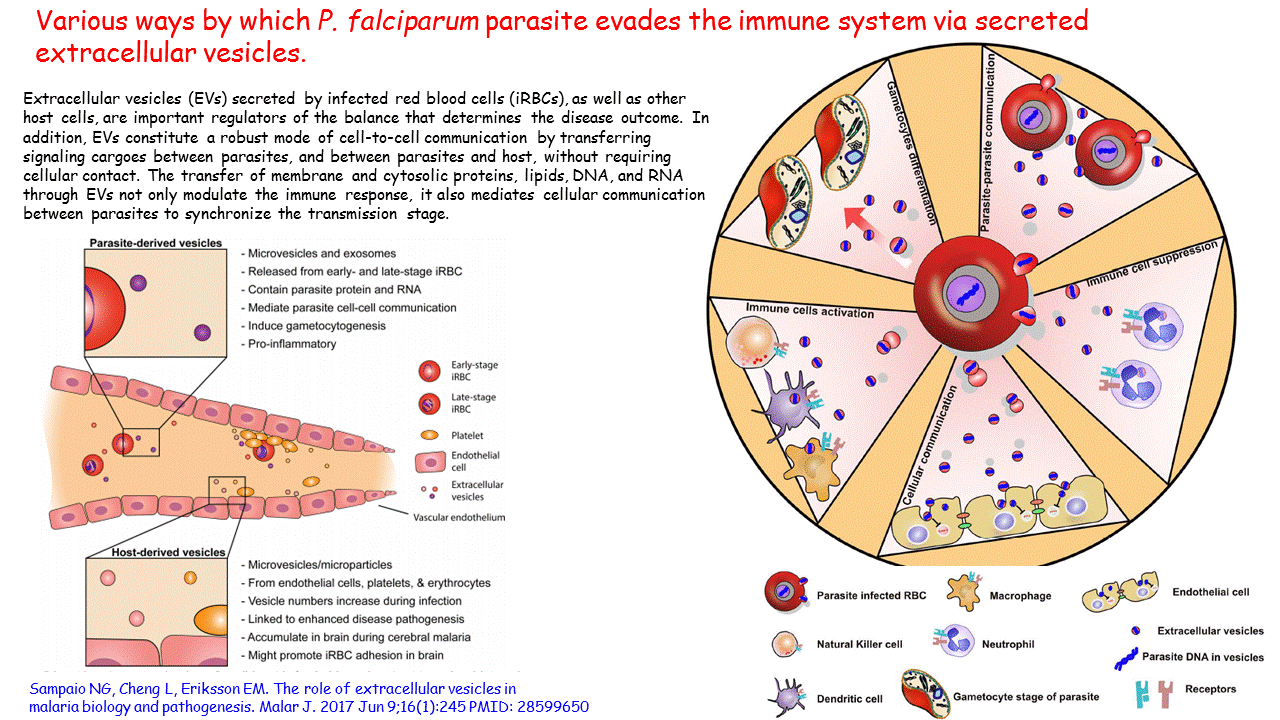 Various ways by which P. falciparum parasite evades the immune system via secreted extracellular vesicles10 junho 2024
Various ways by which P. falciparum parasite evades the immune system via secreted extracellular vesicles10 junho 2024
você pode gostar
-
 Boruto: Two Blue Vortex' Chapter 3 Release Date And Time Confirmed10 junho 2024
Boruto: Two Blue Vortex' Chapter 3 Release Date And Time Confirmed10 junho 2024 -
 Rangoon creeper - Encyclopedia of Life10 junho 2024
Rangoon creeper - Encyclopedia of Life10 junho 2024 -
 Ellen Page thinks Naughty Dog “ripped off” her likeness for The10 junho 2024
Ellen Page thinks Naughty Dog “ripped off” her likeness for The10 junho 2024 -
:max_bytes(150000):strip_icc()/House-of-the-Dragon-Syrax-Caraxes-080822-0dcff8e5a04246ecb41fbcefe6fd5e9c.jpg) House of the Dragon: A scientific guide to the dragons of Westeros10 junho 2024
House of the Dragon: A scientific guide to the dragons of Westeros10 junho 2024 -
 EMERGENCY VEHICLE - SW4 SAMU (BRASIL) - GTA5-Mods.com10 junho 2024
EMERGENCY VEHICLE - SW4 SAMU (BRASIL) - GTA5-Mods.com10 junho 2024 -
 Fundo De Ilustração De Tiro De Jogo, Jogos, Armas De Fogo, Tiro Imagem de plano de fundo para download gratuito10 junho 2024
Fundo De Ilustração De Tiro De Jogo, Jogos, Armas De Fogo, Tiro Imagem de plano de fundo para download gratuito10 junho 2024 -
 Christmas - Papa's Sushiria To Go (Part 11)10 junho 2024
Christmas - Papa's Sushiria To Go (Part 11)10 junho 2024 -
 DRE Butantã recebe formação do PROSPIC Secretaria Municipal de Educação - Secretaria Municipal de Educação10 junho 2024
DRE Butantã recebe formação do PROSPIC Secretaria Municipal de Educação - Secretaria Municipal de Educação10 junho 2024 -
 Paramount lançará edição de aniversário de Tomb Raider10 junho 2024
Paramount lançará edição de aniversário de Tomb Raider10 junho 2024 -
Today the official mascot, logo and hashtag of the FIDE Chess Olympiad 2022 has been unveiled by the Chief Minister of Tamil Nadu M.K.…10 junho 2024

